BATTLEFIELD: PLAY4FREE
ARGUMENTS INJECTION
Luigi Auriemma1and Donato Ferrante2
ReVuln
http://revuln.com
info@revuln.com
http://twitter.com/revuln
22 March 2013
Abstract This paper describes a remote code execution vulnerability in
Battlefield Play4Free3. The vulnerability was first presented by the authors
at Black Hat Europe 20134, as part of a talk covering several interesting
aspects related to games security.
1 SOFTWARE DESCRIPTION
From Wikipedia5: "Battlefield Play4Free (sometimes abbreviated BF: P4F) is a first-
person shooter video game developed by EA Digital Illusions CE and Easy Studios
and published by EA. Based on the Battlefield series, the game features a modern
warfare battlefield setting. Play4Free is built on a modified version of Battlefield
2’s game engine with improvements such as high resolution artwork and post-
processing effects. The game is also less demanding on computer specifications,
similar to Battlefield Heroes.
Figure 1: Battlefield Play4Free
As the game’s title suggests, the game is available to players for free online, un-
der Electronic Arts’ "Play4Free" model. Play4Free uses a similar micro-transaction
store system similar to that in Battlefield Heroes."
1http://twitter.com/luigi_auriemma
2http://twitter.com/dntbug
3http://battlefield.play4free.com
4http://www.blackhat.com/eu-13/briefings.html#Ferrante
5http://en.wikipedia.org/wiki/Battlefield_Play4Free
ReVuln - http://revuln.com page 1 of 8

2 VULNERABILITY DESCRIPTION
Battlefield Play4Free is based on the Frostbite6game engine and it shares the same
architecture with Battlefield Heroes7. The game architecture will be described first,
in order to get a better understanding of the issues affecting the game.
2.1 GAME ARCHITECTURE
An overview of the game architecture is shown in the following image:
Figure 2: Battlefield Play4Free architecture
The interaction among these three components is the following:
•The Browser Plugin exports the following method to the browsers, so any
website can call these functions:
–Start( bstrCmdLine, bstrDotnetfxUrl );
•When Start is called the Game Plugin executes the following code:
–CreateProcessW("B*Updater.exe %bstrCmdLine% -host %website%");
•%website%, the website calling the Start function, is checked against a whitelist8
by the Game Updater component.
–Only websites in the whitelist can use the Game component
•The Game Updater checks the game version and executes the Game by using
a command line, which may contain the following arguments:
–dc, lang, sessionId, soldierName
Please note that the arguments are passed from the Game Plugin as is to the
Game component. Most interestingly, the Battlefield Play4Free soldierName argu-
ment can be abused.
6http://dice.se/frostbite/
7http://www.battlefieldheroes.com
8See Appendix A for details
ReVuln - http://revuln.com page 2 of 8
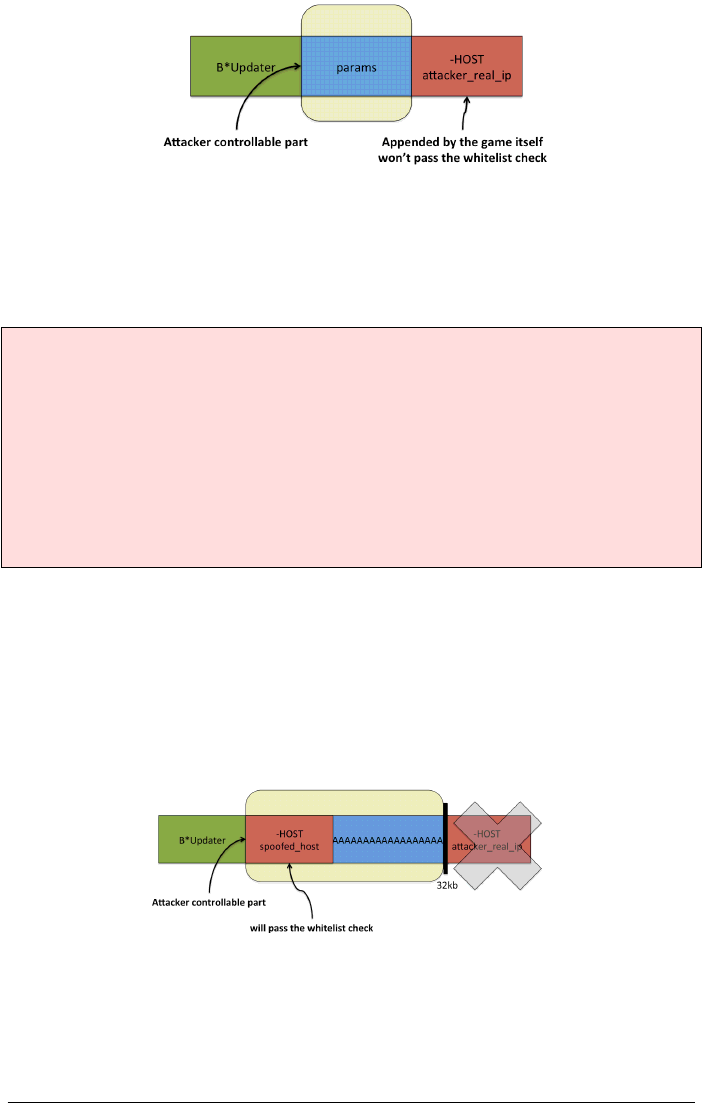
2.2 CREATEPROCESSWAND HOST WHITELIST BYPASS
The Game Updater component performs a whitelist check for security reasons, to
prevent games running from malicious (non withelisted) hosts. The following im-
age gives an idea of how the command line is handled by the game:
Figure 3: The whitelist check in action
The vulnerability is exploitable only on Windows XP an 2003, due to the way the
CreateProcessW API works for these versions. The CreateProcess function is defined
as follows:
BOOL WI NAPI Cr eat ePr oce ss (
_In_opt_ LPCTSTR lpApplicationName ,
_Inout_opt_ LP TSTR lpCommandL ine ,
_In_opt_ LPS ECUR ITY_ ATT R IBU TES lp Pro cessAttr ibutes ,
_In_opt_ LPS ECUR ITY_ ATT R IBU TES lp ThreadAt tributes ,
_In_ BOOL bInheri tHand les ,
_In_ DW ORD dw Creatio nFlag s ,
_In_opt_ LPVOID lpE nv ironment ,
_In_opt_ LPCT STR lpC urrentDi rectory ,
_In_ LPSTART UPI NFO l pStartupI nf o ,
_Out_ LPPROCESS_INFORMATION lpProcessInformation
);
Consider function parameter LPTSTR lpCommandLine. The CreateProcessW (not
CreateProcessA) function handles this parameter differently depending on the ver-
sion of Windows in use on the system. Specifically, prior to Windows Vista, if
lpCommandLine is longer than 32kb, CreateProcessW truncates lpCommandLine to
32kb, and executes the command. For Windows Vista and later versions, it termi-
nates. The following image shows a tricky way to bypass the whiltelist check:
Figure 4: Bypass the whitelist check by padding out the real host
ReVuln - http://revuln.com page 3 of 8
2.3 TARGETING WINDOWS XP
Battlefield Play4Free has been available since 2011, and it requires DirectX 9 in
order to run. The game uses a low amount of system resources and it is used on
Windows XP systems too. Issues affecting Windows XP are still valuable. As of
March 2013, Windows XP has about 40% of the market share9.
2.4 THE ROOT CAUSE
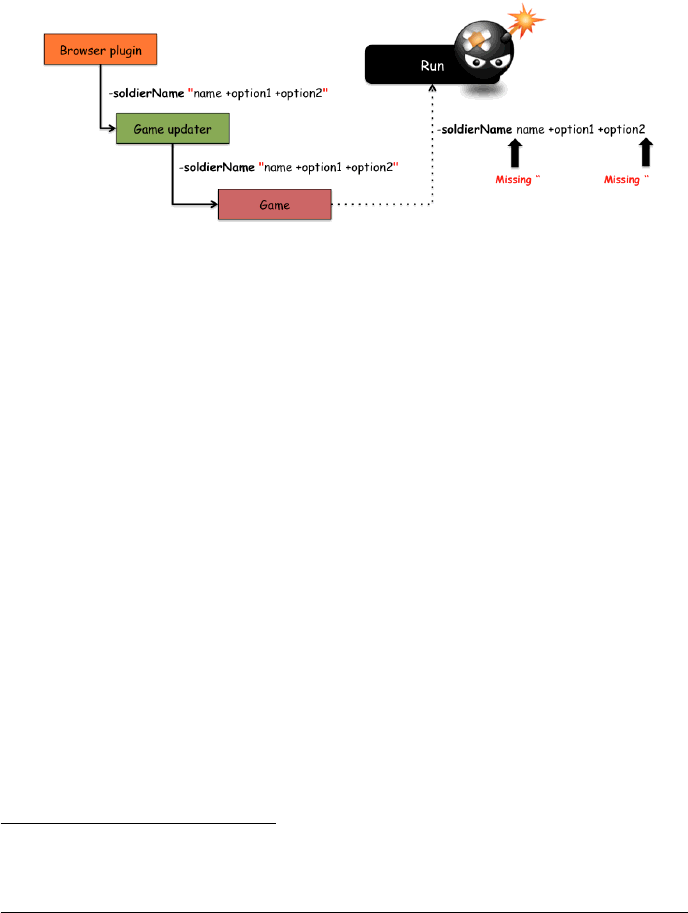
The game allows us to exploit the soldierName argument as the Game Updater sup-
ports the char " (double quote), while the Game component doesn’t. Because of
that it is possible for an attacker to inject arbitrary sequences of "arguments". The
following image shows the problem by detailing how each components handles a
given command line string (bstrCmdLine):
Figure 5: Components handling bad arguments
It’s interesting to note that Battlefield Heroes is not affected by this issue, since
its Game Updater component doesn’t support the double quotes for soldierName
option. Please keep in mind that this vulnerability is limited to Windows XP, due to
the way the Browser Plugin spawns the process using CreateProcessW.
2.5 POSSIBLE ATTACK PLAN
To exploit the vulnerability, the +modPath option was used to specify a directory
containing game mod data (sounds, map, etc..). Mod data is usually composed of
ZIP files and CON files to configure the Frostbite game engine. Interestingly, the
+modPath option can refer to arbitrary paths, which may include SMB/WebDAV
locations. In general the +modPath option is used to load files, such as RankSet-
tings.con. Consider the idea to craft a RankSettings.con file, to invoke the following
commands on the game engine:
•sound.addSound
•ObjectTemplate.soundFilename
•sound.listSoundsToFile
To make the attack more stealthy an attacker can add Game.crash to the sequence
of commands above. This will cause the program to terminate just after executing
all the commands.
9http://en.wikipedia.org/wiki/Microsoft_Windows#Usage_share
ReVuln - http://revuln.com page 4 of 8

2.6 +MODPATH EXPLOITATION: STEP 1
This section describes the approach used to demonstrate the vulnerability. The
following sequence of commands were used:
•sound.addSound
–specifies the name of the sound resource
•ObjectTemplate.soundFilename
–used for commands, note:
∗the double quote char (") cannot be used and no escape char is
available
∗the comma char (,) is used to delimit file names, for example,
"hello, world" is split in 2 lines with the comma removed
∗each line will be converted to lowercase
∗each line must be unique, and duplicates are discarded
∗each line generated is followed by the string:
;0.000000;0.000000;0;0.000000;0;0;UNKNOWN
∗all backslashes will be converted to forward slashes
∗each line can be a maximum of 1024 bytes due to a sprintf_s
∗the usage of % is limited due to a format string bug
•sound.listSoundsToFile
–stores the commands in a file
2.7 +MODPATH EXPLOITATION: STEP 2
It’s important to keep in mind the following limitations:
•UNC paths are excluded because backslashes are converted to forward slashes
•ftp.exe
–doesn’t support passive mode, and the non-passive mode will trigger
the firewall
•vbs
–soundFilename limitations make its usage very difficult, although a good
option for a download&execute approach
•telnet -f
–limited to text data
•rundll
–comma not allowed
•webdav
ReVuln - http://revuln.com page 5 of 8

–available from XP to Windows 8 except for 2003 (disabled), as a manual
or automatic service10.
•tftp.exe
–available by default on Windows XP, it works on udp, and it’s not limited
by the firewall
2.8 +MODPATH EXPLOITATION: STEP 3
To demonstrate the vulnerability, tftp.exe was used. This is probably the best choice
since only Windows XP and 2003 are affected by the vulnerability. The following
describes how to bypass the limitations:
•use && in the batch file to avoid handling the string
";0.000000;0.000000;0;0.000000;0;0;UNKNOWN":
•use %% instead of % to avoid the format string vulnerability:
•the %TEMP% folder was chosen because Windows XP uses 8.3 expansion,
alternatively fixed paths could be used, such as: c:\windows\temp, etc.
The proof of concept video provides several additional details on how an at-
tacker may exploit this issue.
3 PROOF OFCONCEPT
A proof of concept video11 showing how to spawn a reverse shell is available on
our Vimeo channel12. The video shows all steps described in this paper.
4 APPENDIX A: WHITELIST
The following are the whitelisted domains, for the host check performed by the
game:
•159.153.184.131
•dice-mdraper1.dice.ad.ea.com
•dice-jtarnstro1.dice.ad.ea.com
•easy-bfh-dev-trunk
•easy-bfh-test-trunk
•easy-bfh-test-release
•preprod.battlefield.play4free.com
•battlefield.play4free.com
•pte.battlefield.play4free.com
•preprod.battlefield.play4free.com
10http://batcmd.com/windows/xp/services/webclient/
11http://vimeo.com/61364094
12http://vimeo.com/revuln
ReVuln - http://revuln.com page 6 of 8

5 FAQ
The following FAQ provides additional information about the issue described in
this paper.
•Is this issue exploitable only on Windows XP systems?
–Yes, XP and 2003.
•What are the affected versions of the components?
–Plugin component version 1.0.80.2, and Game component 1.52.245751.0
•I can’t reproduce the issue, why?
–Because EA, after our paper, fixed on 25 March 2013 the issue with a
new release of the Plugin component, version 1.0.95.0
ReVuln - http://revuln.com page 7 of 8

